Verifiable CredentialsFramework
Make information easy to verify, and impossible to fake.
In this third age of the internet, Web3, we need a new paradigm for exchanging and verifying information. We need to put users back in control of their data, while creating a framework for trust that doesn't rely on big platforms or strong central government. EBSI's Verifiable Credentials Framework is a full framework for expressing, exchanging, and verifying information, using a new information format (W3C Verifiable Credentials), digital wallets, and the blockchain to establish trust.
History
WEB 1.0
![]()
WEB 2.0
A trust model relying on trusted third parties.
![]()
WEB 3.0
A trust model relying on Verifiable Information.
EBSI provides the elements of a Web 3.0 trust model
We combine three key technologies to enable trusted, decentralised information exchange:
Verifiable Credentials
A new format for expressing information that is almost impossible to fake.
Digital wallet
Conformance-tested apps built according to EBSI's specifications that allow users to manage credentials and keys while maintaining control - their personal data is never stored on ledger.
Blockchain ledger
Highly available and resilient source of information using permissioned Trust Registers deployed on EBSI’s Blockchain to support verification.
A new information sharing pattern
In today’s information landscape, information and documents such as ID cards, diplomas or driving are easy to fake and difficult to verify.
Verifiers rely on the Issuers to trust the information they receive. Since they need to maintain relationships with many issuers, the verification process is by nature very complex and time-consuming. In addition, issuers (e.g. Countries and institutions) use different formats, documentation and databases (as well as different processes, technical stacks and semantics, etc.) e.g. making it very difficult for verifiers to automate and/or verify credentials. When information is hard to verify, centralised intermediaries and platforms become the source of trust.
The centralization of information in big tech platforms has resulted in a loss of privacy and control over personal data, as these platforms have gained a dominant position in the digital landscape. EBSI and Verifiable Credentials propose a new pattern for exchanging information. In this pattern, the Verifier and Issuer are never in direct contact with each other. Instead, the citizen manages their information in their wallet and the verification process is enabled by blockchain. This is a self-sovereign and privacy-preserving way of ensuring that information can be trusted.
This is why EBSI’s investing in technology that helps us easily verify information.
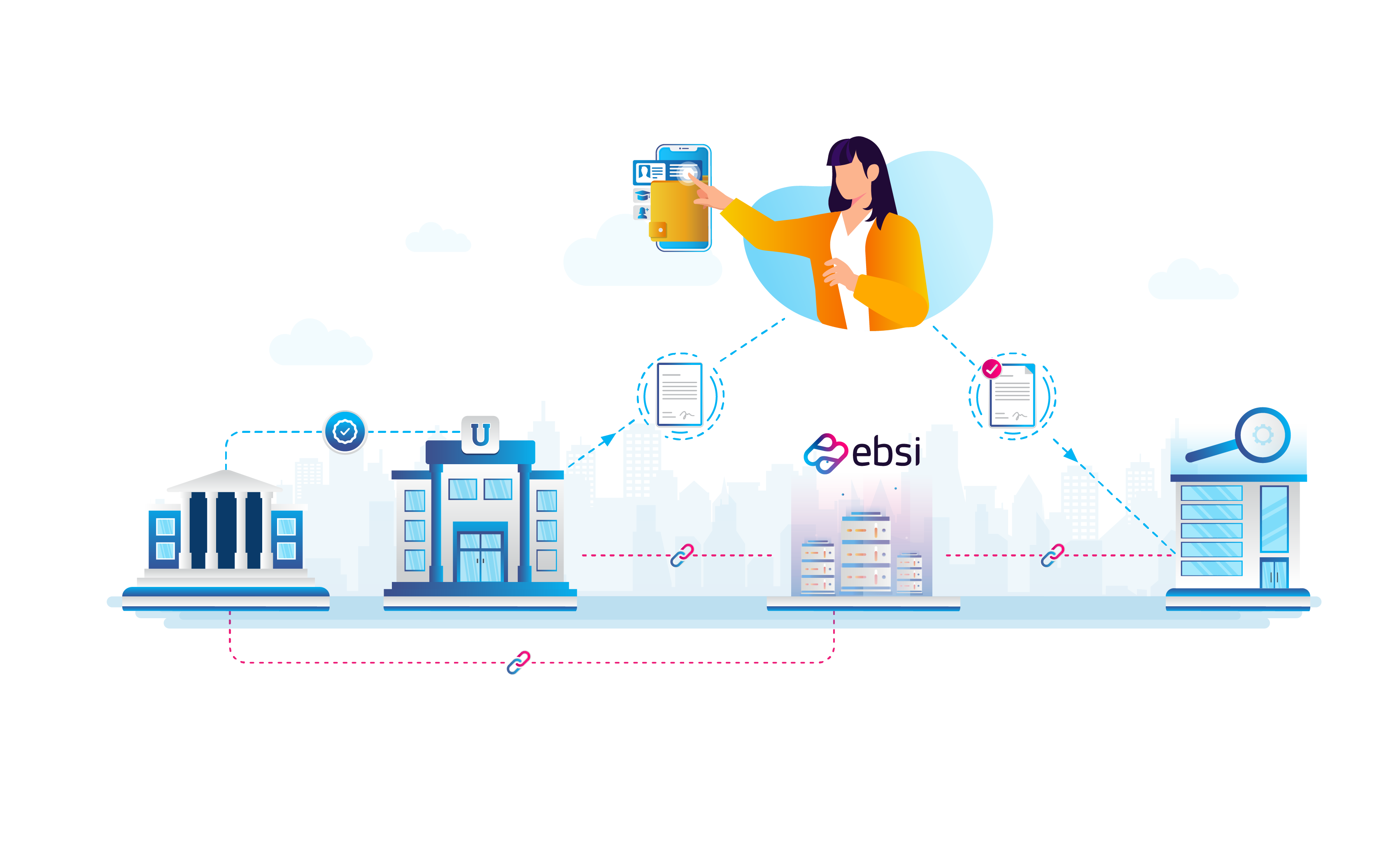
Understand the EBSI ecosystem
By clicking on the visual, you will learn more about the actors and ter role in the EBSI ecosystem as well as the key concepts usefull to understand blockchain applied cross border sevices.

Trusted Accreditation Organisations(TAO)
In Verifiable Credentials use cases, a TAO is an organisation that can accredit an issuer with the ability to issue certain types of Verifiable Credentials.
Trusted Issuers
In Verifiable Credentials Use Cases, the Trusted Issuer is a role that a Legal Entity might perform by creating a Verifiable Credential, associating it with a specific subject, and transmitting it to a holder. The Issuer is trusted as its accredited by a TAO, the accreditation is stored on the ledger and can be verified later. For example, issuers include governments, businesses, non-profit organisations, trade associations.
EBSI
EBSI's blockchain ledger is a decentralised database that keeps a record of all transactions written on it. The information is stored in blocks that are cryptographically linked to each other, forming a chain - hence "blockchain"- making the information almost impossible to tamper with. On EBSI ledger, we make available specific registries that can be used by the Use Cases as a source of trust. For example, EBSI's Trusted Issuers registry can be used in the education domain to keep a tamper-evident record of all universities accredited by a national educational body, increasing trust and making verification of diploma credentials much easier.
Trusted Verifiers
It is a role an entity performs by receiving one or more Verifiable Credentials, optionally inside a verifiable presentation, for processing. For example, an employer will verify the authenticity of a verifiable diploma shared by the student (holder).
Holders of Credentials
The holder of a Verifiable Credential sits at the center of a triangle of trust, mediating between issuer and verifier. The issuer and holder trust each other, the holder trusts the verifier, and the verifier trusts the issuer. Any role in the triangle can be played by a person, an institution, or an IoT-device. The holder of the Verifiable Credential, issued by the issuer, is most often an individual, but it can also be an organization. He is the sole owner of the issued Verifiable Credential, and has full control over its handling, use and verification
Register to EBSI
This is the process that will allow the TAO to get accredited and register the information on the EBSI Trusted Issuers Registry.
Issue Verifiable Credentials
This is the process taken by a Trusted Issuer to issue a Verifiable Credential addressed to a Holder.
Register to EBSI
This is the process that will give access to the EBSI DID Registry and enable the Trusted Issuer to register the DID and DID Document on the EBSI Ledger.
Verify VCs using EBSI
This is the process taken by the Verifier to verify the authenticity of the Verify Credentials shared by the Holder on the EBSI Legder.
Present VCs as Verifiable Presentations
This is the process taken by the Holder to exchange on or more Verifiable Credentials with a Verifier.

Verifiable Credentials
It is a digital document format based on the W3C open standard for Verifiable Credentials. EBSI's Verifiable Credentials profile uses this W3C standard to ensure interoperability and wide adoption. They can represent information found in physical credentials, such as a passport or license, as well as new things that have no physical equivalent, such as ownership of a bank account. They have numerous advantages over physical credentials, most notably that they're digitally signed, which makes them tamper-resistant and instantaneously verifiable.
Verifiable Presentation
A verifiable presentation expresses data from one or more Verifiable Credentials, and is packaged in such a way that the authorship of the data is verifiable. If Verifiable Credentials are presented directly, they become verifiable presentations. Data formats derived from Verifiable Credentials that are cryptographically verifiable, but do not of themselves contain Verifiable Credentials, might also be verifiable presentations. The data in a presentation is often about the same subject, but might have been issued by multiple issuers. The aggregation of this information typically expresses an aspect of a person, organisation, or entity.
Want to understand in details how EBSI works?
Discover Verifiable Credentials domains
Every organisation issues, holds, and verifies credentials. Every person holds credentials. From a licence to operate a business to a licence to drive a car, from the information on a product shipment container to a product organic label, everyone needs to make or verify claims throughout their lives. EBSI's Verifiable Credentials Framework offers an answer

EBSI Specifications
If you have already defined your use case, you might be ready to start your design process. EBSI has developed the Specifications section to help TAOs, Issuers, Wallet Providers and Verifiers answer key questions and understand how to implement VCs according to W3C and EBSI standards. In case, you want to explore more about our key concepts of EBSI's technology before deep diving into the specifications, you can check out our EBSI Explained series.
Get inspired with our 6 success stories
In July 2021, the “Early Adopters”, 2 European universities alliances and 11 universities from 11 countries joined their forces to create the so-called “multi-University pilot” during which they identified, designed and delivered 6 cross-border scenarios, together.
Get inspired by their success stories below.
Do you also want to pilot?
Join the Early Adopters program and discover how you can register by having a look at our page.
Early Adopters programme