Use of Digital Technologies for the Protection of Public Spaces

date: 10/09/2020

Copyright: Greenbutterfly @adobe.stock
The digital revolution has opened up possibilities for gathering and retrieving immense amounts of data in real time. Technologies which used to be confined to specialized forensic laboratories or to critical infrastructures are now more broadly accessible to local authorities and can be applied for improving the day-to-day protection of public spaces. Data from video-surveillance systems, biometric or digital footprint databases and CBRN (chemical, biological, radiological and nuclear) sensors can be analysed and interlinked to produce sense-making information through facial recognition algorithms, artificial intelligence tools and data analytics.
Harnessing technological solutions provides plenty of opportunities for enhancing the protection of public spaces. Applied and analysed properly, the data derived from IoT (Internet of things) devices can provide information for early threat detection of multiple scenarios (terrorism, crime, natural disasters, pandemics). The availability of tools to gather more complex, comprehensive and quick information can help better-informed and timelier decision-making. Mobile applications and social media platforms can serve as fora for involving citizens in the protection of public spaces. Better communication channels and integrated systems allow for improved coordination and collaboration among different authorities.
These extensive opportunities are matched by equally hefty challenges. In terms of technology, even the best hardware would not be useful without the proper data-analysis software and the trained personnel to handle the information. Different systems must be interoperable if they are to allow for the analysis of data from different sources. Interoperability becomes even a more complex issue if applied to systems used by different authorities, different cities and different countries. Any system must respect the principles of privacy protection enshrined in the General Data Protection Regulation [1]. Technology is a powerful tool for security, but it can be equally powerful as a threat, thus technological protection measures must evolve accordingly.
In this article, we will provide a brief overview of the technologies, which most commonly serve urban authorities and security operators for the protection of public spaces. We will provide tips for choosing the appropriate solutions and highlight considerations for the overall management of technological protection systems. The choice of any technological solution applied must be the product of not only the availability of budgetary and personnel resources, but also of a comprehensive risk assessment procedure with informed analysis of the predominant threat and the vulnerabilities for the particular site or event.
- Video Surveillance, Sound Detection and Collection of Biometric Data
Biometric data refers to body measurements, which provide individual human characteristics through which a person can be identified. Biometric data includes facial features measurements, iris scanning, voice recognition, fingerprint and palm scans, gait analysis and DNA databases.

Figure 1: Most common methods for urban authorities and security operators to use biometric data for the protection of public spaces (concept of the authors, icons from http://thenounproject.com)[2]
Video surveillance technology has been revolutionized with the introduction of high computing power, huge memory potential and ample processing capabilities. Closed-circuit television (CCTV) systems provide real-time monitoring of large areas allowing for the reduction of patrolling personnel. A video surveillance system usually consists of cameras, transmission media, image analysis equipment, monitors, recording and storage systems. The market offers an overwhelming variety of cameras, which may create difficulties in the choice of the appropriate solution for the particular public space.
Among the first considerations in the choice of camera would be the level of detail, the installation point, the desired view and consequently whether it needs to be fixed, equipped with rotating/zooming capacity or multi-lens technology. The quality of the video image does not only depend on the resolution (HD, Full HD, 4K etc.) of the camera, but also on the surrounding lighting, the contrast of the various items relative to the background, the complexity of the environment and the movement of objects or personnel. The choice of the resolution capacity depends on the intended application (detection, face or number plate recognition etc.). Stored images can only be zoomed digitally (in contrast with real-time recordings) so their resolution needs to be high enough to provide crisp and clear results.
The operational conditions would also determine the imaging and light sensitivity requirements, as there are visual monochrome and colour cameras, models that can function under night conditions with extremely low light demands (ICCD cameras), and cameras that use thermal sensors and can operate in total darkness (thermal cameras). The transmission of the video signal (analog or digital) to the monitor may have to be broadcasted through buildings, the ground etc., so the hardware to be used (cables, optical fiber, LAN, internet, wireless etc.) needs to be carefully selected to satisfy the video signal quality requirements. Table 1 summarizes the most important characteristics of the surveyed area and the viewing equipment that have to be considered from the decision makers before setting up a video surveillance syste

Table 1: Video surveillance considerations
Sound detection or audio monitoring, when combined with the appropriate software, can automatically filter natural/common noises and distinguish abnormal sounds that are of human (e.g. a scream) or other (e.g. class breaking, gunshots, explosions) origin. Sounds are screened and classified based on their acoustic features and trigger an alarm if they correspond to certain characteristics.
The advantage of audio surveillance systems is that they can still operate under low or no light conditions, where video systems may not provide clear images, and they can have a supporting role to images captured by a CCTV, providing additional verification in case of an incident. The effectiveness of such systems is lower in noisy environments with multiple sound sources, as they have to separate background noise from the alarm-triggering sounds. With the advent of machine learning techniques, the identification of threat sounds (e.g. gunshots) has become more accurate thus reducing false alarms. Moreover, the distribution of multiple sensors in city areas also allows the identification of the event location thus allowing targeted law enforcement actions.
Other biometric identification methods, like iris scans, fingerprints and palm identification can be used for access control of authorized personnel in buildings. These technologies provide a simpler (in terms of the volume of algorithm input) and not so easily alterable method for identification. The major drawback of these technologies is that a database with the biometric data of all authorized personnel must be kept by the security services and be accessible by the control device, which creates risk for hacking the database with malicious intentions. Such systems can also be more cumbersome than conventional solutions like badge readers or pin code-based access authorizations.
Video surveillance and sound detection technologies are not flawless. They can pose technical problems like lack of accuracy (for example, blurred image, bad quality sound or false alarm due to noise pollution) or blind spots in coverage. If the system was created in different phases, there may be discrepancy in the formats of the footage different video cameras are producing, which would hamper the analysis. It is important to provide for regular preventive and corrective maintenance of the hardware and update of the analysis software. Lack of ample data storage, proper filing plan and defined procedures for retaining and archiving of footage files can cause loss of data or delays in the data analysis. Another major drawback is that video surveillance cameras accumulate immense amounts of footage [3] which has to be thoroughly analysed by security operators if an incident is to be prevented or meticulously sieved through in case an incident materializes.
Figure 2: The immense amounts of data surveillance technology generates, can hinder its analysis and thus render it futile (concept of the authors, icons from [4])
- CBRN-E sensors
Even if the accessibility to substances required for creating Chemical, Biological, Radiological, Nuclear and Explosives (CBRN-E) agents or devices is usually limited, terrorists might still be able to possess them, enabling them to perform an attack. To facilitate better understanding and improved cooperation between Member States, the European Commission issued a dedicated Action Plan [5] that proposes several actions to contribute to the preparedness and resilience in case of a CBRN-E attack. Sensors detecting CBRN-E threats, that includes more than one thousand agents, used to be the domain of secret services and highly specialized personnel. In the last years more accessible technologies allow for almost real-time detection by trained security operators.
Various technologies can be employed for detecting the presence of dangerous agents: for example, ion spectrometry for tracing chemicals and explosives, gamma-ray spectrometry for radiological agents or polymerase chain reaction assays for detecting biological threats. Such technologies are extensively used in the civil aviation field to identify the unique attributes and chemical components of CBRN-E agents (focusing mainly on detection of explosives and weapons). X-ray scanners, which use computerized tomography, can detect explosives hidden in bags or suitcases, but they have their drawbacks especially in the face of improvised explosive devices or mouldable plastic explosives, the shape of which cannot be easily recognized through an X-ray scan.
The market offers equipment which can detect the majority of hazardous agents. Selecting an appropriate sensor depends on the established attack scenario and the relevant risk analysis. Attacks with the use of CBRN agents are of low probability but could potentially have a great societal impact. The detection of an ample range of agents may require the use of multiple systems that have to work together through a dedicated interface, which may increase operational complexity. The optimal and accurate sensor placement following a detailed study on the facility’s needs is essential for minimizing their number (combination of protected area and sensor coverage range) and keeping low the initial, operational and maintenance costs.
- Access Control
Access control systems serve to block the entry of unauthorized or suspicious individuals or threatening objects to public or private spaces. Badge readers are commonly used to control entering personnel by validating identity data saved on a chip on the card through magnetic stripe or proximity reader. Touchpads requiring a code or biometric scanners (fingerprint or retina) can also be used for access control. Often, usually at crowded events or public buildings, metal detectors are used for checking of unauthorized metal objects, but they may have the drawback that they are not sensitive towards non-metallic weapons. Full-body scanners (millimetre-wave or X-ray) can detect also non-metallic objects concealed on a person’s body, but have the disadvantage of significantly slowing down the flow of people and of being relatively expensive. Full-body scanners are strictly regulated by EU regulations and must meet operational requirements and detection performance standards [6].
To ensure that access to restricted areas is prohibited, various intrusion detection systems may be used, such as glass break sensors, laser scanners, motion and radar detectors, magnetic contacts, pressure-sensitive mats, trip wire sensors and volumetric surveillance sensors.
- Internet of Things, data from smart city sensors
Our cities are interweaved with sensors from public transportation and road traffic networks, energy, communication or transactional infrastructure, civil security and law enforcement agencies, public interest networks and myriad of other services. The Internet of Things concept refers to the computing devices embedded in everyday objects, which can send and receive data. These sensors generate huge amounts of data referred to as “big data”. Urban security can profit from information produced by these sensors. Knowing where the traffic is blocked in a city, or the hours and zones in which traffic is at its peak could provide decision makers with a good basis for the vulnerability assessment of assets during varying traffic conditions. Unified security systems deal with complex and diverse data from video surveillance, licence plate recognition and access control tools that is mixed with data from traffic lights, traffic or communication sensors providing a very good overall picture of incidents in real time.
Unifying the numerous sensors and data sources in public spaces opens up the way for seamless data-sharing and more collaboration among different authorities and security providers. The smart city concept model is laid out in ISO/IEC 30182:2017 “Guidance for establishing a model for data interoperability” based on the alignment of ontologies used in the data emitted by different sensors. Using the potential of this fast-growing field requires decisions on the software tools, hardware platforms and data protocols in order to ensure efficient data access and sharing. Without sharing, “big data” cannot work – its potential is harnessed only when it is “big”, but sharing data in the field of security will have to be done through strictly defined secured channels and protocols. The tools for anonymizing such data without rendering it useless for security purposes is also an ongoing debate which will have to be resolved for the benefits big data offers when used at its full potential.
- Real-time data mining and data analytics
Thankfully, the revolution in hardware tools has been paralleled by significant developments in technologies for analysing the data obtained by video surveillance cameras, sound detection devices or Internet of Things (IoT) sensors.

Figure 3: Making sense of data through data-analytics techniques
Data-mining refers to uncovering trends or patterns in big chunks of data, while real-time is the capacity to provide the crunching of data instantaneously. Text mining, for example, is a data-mining technique, which allows for the processing of huge amounts of text and aggregate it into trend patterns according to the users’ needs. The Europe Media Monitor [7], for example analyses both traditional and social media aggregating data from 300,000 news articles per day from world-wide news portals in up to 70 languages. The Joint Research Centre of the European Commission is developing an open-source tool which analyses terrorism incident data collected by the Europe Media Monitor which are useful in assessing emerging threats and terrorism tactics.
Data-analytics is about extracting, cleaning, transforming, modelling and visualizing the data and converting it to meaningful information or hypotheses deemed useful to decision makers. The output of data analytics can be descriptive (what happened), diagnostic (why it happened), predictive (what might happen) and prescriptive (recommend action based on the forecast). The capacity of video-surveillance systems is not only due to the broad availability of hardware, but also due to the elaborate software solutions which can be applied to analyse the data collected.
Such systems are widely used to automatically recognize vehicle number plates that enter into restricted access zones (e.g. in historic city centres), for speed checks and police enforcement purposes. The algorithms used for security checks can be divided in three categories serving different objectives as shown in Table 2.
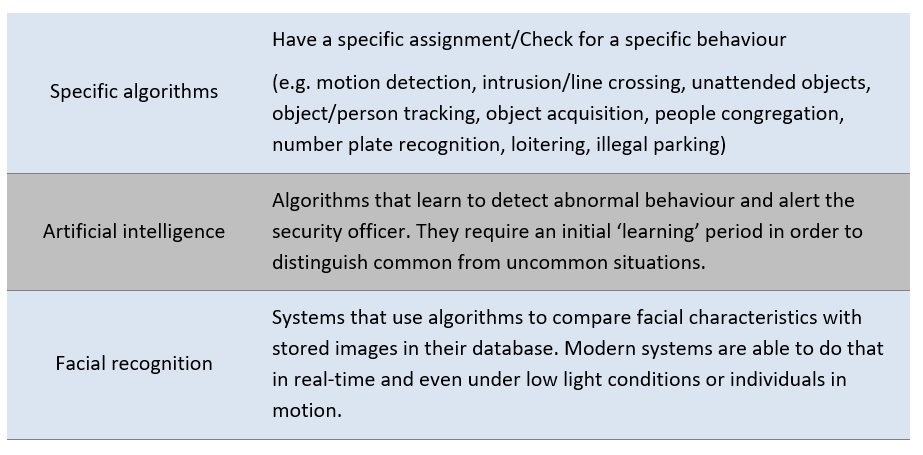
Table 2. Video analysis algorithm types.
For the purposes of protecting public spaces, facial recognition can facilitate the identification of suspicious individuals in a crowd by comparing real-time images sent by surveillance cameras with a database of images of potential perpetrators. More advanced technologies can incorporate facial recognition algorithms with other biometric data like gestures, gait, body mass or with personal objects (watch, handbag, jewellery) for higher precision in the identification. New artificial intelligence (AI)-based analytics software can help in reducing the effort of constantly monitoring real-time video footage. Such systems can, for example, identify non-standard situations (e.g. people gathering), perform geofencing (i.e. control whether somebody is trespassing certain restricted areas) or identify objects and unattended luggage.
Facial recognition technologies have stirred up a lot of controversy. There is no consensus in the EU on how to apply GDPR concepts as data minimisation, accountability and transparency of AI systems [8]. The machine learning algorithms feeding artificial intelligence systems get “trained” with data from previous incidents or arrests. Such data may be biased, making the algorithm biased thus triggering biased decision making towards particular ethnic or religious groups. The European Data Protection Supervisor favours the use of the precautionary principle and a moratorium on the use of facial recognition technologies until their impact on society and individual freedoms are clarified and regulated [9].
Big data analytics refers to the systematic extraction of information from huge, often heterogeneous data sets. It is the way to convert all the data from smart city sensors and the Internet of Things to sense making information. Big data analytics is a highly dynamic field, where significant improvements in available technologies are announced daily. The field faces significant challenges like problems of interoperability (how to compare data from different sources measured in different time lapses and using disparate metrics), accessiblity (who has access to the data), accountability (how was the data analysed in order to arrive to certain information), storage (not only the size but also the geographical location of the servers, how long is the data to be retained), cyber-security (how to protect the data and the outputs from hackers), and, definitely not least, compliance with the GDPR.
Smart City platforms offer the environment for data collection from city sensors and the possibility to integrate with urban intelligence analysis. As an example, FIWARE [10] is an open source cloud platform developed under the initiative of the European Commission in order to provide a space for small and medium size enterprises to make full use of the potential presented by the growth of smart city data and interconnectivity. Such system allows for the integration of heterogeneous devices and sensor networks and the coordination of different systems. The core of such system, the EC connective Europe facility (CEF) Context Broker, is designed to allow the management and sharing of contextual data in real-time. Some examples include Smart Security scenarios with the integration of video streams analytics. However, the convergence of Smart City systems and Security/Surveillance systems is usually challenging because of different roles and information confidentiality of the city management and law enforcement departments.
- Mobile phone applications
Mobile phone applications may allow for the participation of citizens to the protection of public spaces. As the Urban Agenda orientation paper [11] states: ‘An integrated approach to safety has at its heart the local social stakeholders, valuing their contribution in terms of both understanding of local needs and sharing of responsibilities related to the care of the places and relations. The involvement of local people and social players in fact strengthens the sense of «presence» of the community in the local area, recognizing the role of protection and support of the perception of greater safety.’ Under the Horizon2020 programme [12], the European Commission has funded several projects to develop mobile phone applications in the field of security.
The experience from the COVID-19 related mobile phone applications brings about lessons that can be applicable to the protection of public spaces. The effectiveness of such applications depends on various factors: the number of users they attract, the trust of the users that their data will be protected and used only as agreed, the ability of authorities to use the data generated by such applications in their decision-making, integration and data sharing with other systems and applications, cross-border and cross-regional interoperability with other systems [13]. Experience shows that if such applications are to be effective they have to be developed including different stakeholders: security operators, urban authorities, data protection authorities, experts and researchers, the private sector, citizens groups.
The European Commission has recommended [14] the development of a Toolbox of digital means to address the COVID-19 crisis. The Toolbox will be based on a pan-European approach for the use of mobile applications coordinated at EU level and on a common scheme for using anonymized and aggregated data. Similar levels of cooperation and coordination at EU level are necessary if mobile apps for the protection of public spaces are to be effective.
- Data Protection
Any technology collecting data related to EU citizens must respect the EU General Data Protection Regulation (GDPR) [15], which harmonizes data privacy laws across the EU with the aim of protecting EU citizens from privacy and data breaches. The GDPR applies to the processing of personal data by controllers and processors in the EU, the processing of personal data of data subjects and the monitoring of behaviour that takes place within the EU. It establishes the rights of data subjects defining rules on granting and withdrawing consent to use persona data, the right to access users’ personal data and the way it is being used, the right to be forgotten (i.e. to request erasure of personal data), ability to use data collected by one controller for another controller (data portability). The GDPR establishes the concept of privacy by design, which means that a controller collects and retains only the data which is absolutely necessary for the performance of its duties (data minimization and proportionality) and limits the access to personal data to those processing it (data anonymization).
Another directive which is relevant to the use of technologies for the protection of public spaces is the EU Directive for the protection of personal data processed for the purpose of criminal law enforcement [16] which applies the principles of the GDPR to the specificities of law enforcement needs. The main objectives of the directive are to better protect individuals’ personal data when it is processed by police and criminal justice authorities and to improve cooperation in the fight against terrorism and cross-border crime in the EU by enabling exchange of information between police and criminal justice authorities (both in terms of national and cross-border cooperation). Compliance to the directive includes the designation of a data protection officer to help the competent authorities ensure compliance with the data protection rules as well as the requirement to carry out an assessment of potential impact where a type of processing has a high risk of breaching an individual’s privacy.
Despite the adoption of the GDPR and the Directive for the protection of law enforcement data, national legislations and local level practices across the EU diverge. The rapid development of technologies which can be employed in the field of protection of public spaces requires continuous re-examination of the application of GDPR principles and what they mean precisely for a given technology or tool. Such considerations can be thoroughly developed only through an open debate among all relevant stakeholders.
- Societal impacts
The use of surveillance technologies may have a “chilling” psychological effect, where people may feel inclined to adapt their behaviour to a norm and this shifts the balance of power between the individual and the state or the organization using surveillance [17]. That means that even if the use of the technology is in full respect of the GDPR, its use may still be intrusive of citizens freedoms and integrity. A well-observed problem is the bias of AI systems – for example algorithms which are trained on data from men or Caucasians leading to broader error margin for women or individuals of different race, also algorithms bear the biases of their developers and cannot be completely neutral [18].
There are calls for designing and creating security technologies with human rights, democracy and rule of law taken in consideration from the outset of the project – the so called “Human Rights, Democracy and Rule of Law by design” [19] underpinned by an obligation to perform Human Rights, Democracy and Rule of Law Impact Assessment before deploying the technology. AI is subject to the same laws governing all other technologies, but some specific characteristics of AI technologies make them more elusive to legal evaluation – for example their opacity (the so called “black-box effect”), complexity, unpredictability and partially autonomous behaviour [20].
In its White Paper on Artificial Intelligence [21], the Commission proposes a risk-based approach to evaluate the need for modifying existing regulations to address the challenges posed by artificial intelligence based technologies. It is likely that technologies used for the protection of public spaces would more often than not fall under the high-risk category. The White Paper states that a broad European debate will be launched to gather and address societal concerns to the use of AI in public places.
- Protecting the technologies for protection of public spaces
Data, its collection and its analysis, is at the bottom of the technological revolution. The problem with the use of personal data is that once breached, it is difficult (not to say impossible) to rectify. As the trend is to use more and more technological solutions by different actors for the protection of public spaces, this would bring about new vulnerabilities with perpetrators exploiting the weak spots of such technologies. On the one hand, the problem with small-scale autonomous technological systems is that they cannot afford state-of-the-art levels of protection and that they are also probably less efficient as the power of technological solutions lies in the large amounts of data. On the other hand, interconnectedness of different systems in a large-scale security set-up can bring about cascading failures with quick and unpredictable consequences and further reaching ramifications in case of a hacking attack.
Any technological solution applied for the protection of public spaces must integrate security at every stage of the development of the tool. Tools which may be secure when operating in isolation may present vulnerabilities when connected to other systems. There must be continuous risk management of the systems in line with other technological tools employed both within and outside of the organization.
- Conclusions
Technology offers a broad range of opportunities for the protection of public spaces. Technological solutions can assist the prevention of terrorist attacks, can substantially decrease the reaction response time to threats and incidents, can provide for better informed decision-making and increased cooperation, coordination and sharing of data among stakeholders, authorities and Member States. Still, digital technologies cannot serve as a panacea which would cure all issues related to the protection of public spaces. They have to be developed in concordance and integrate with physical protection measures. Technological solutions and their use must be designed to respect privacy regulations. Security operators and urban authorities must be aware of the potential vulnerabilities technological solutions open up and to apply systematic risk assessment, security and maintenance procedures. Accountability, transparency and reliability in operating security technologies are the foundations for public trust. Ultimately, the trust of the citizens is the foundation upon which the effectiveness of technological solutions for the protection of public spaces can be constructed.
- References
[1] Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation) (Text with EEA relevance) OJ L 119, 4.5.2016, p. 1–88; https://eur-lex.europa.eu/eli/reg/2016/679/oj
[2] Icons from The Noun Project https://thenounproject.com as follows: from bottom left clockwise: Voice recognition: Gregor Cresnar; Fingerprint: Eucalyp, Facial Recognition: Vectors Point, Security camera: bmijnlieff ; Iris scan: Nociconist, Crowd: Magicon.
[3] Just to mention one example: After the terrorist bombing of a concert hall in Manchester in 2017, British police had to wade through more than 16,000 hours of CCTV footage. Source: - The Economist. ‘Walls have eyes Street-level surveillance is everywhere.’ Technology Quarterly Jun 2nd 2018 https://www.economist.com/technology-quarterly/2018-05-02/justice
[4] Icons from The Noun Project https://thenounproject.com as follows: from bottom left clockwise: Voice recognition: Gregor Cresnar; Fingerprint: Eucalyp, Facial Recognition: Vectors Point, Security camera: bmijnlieff ; Iris scan: Nociconist, Crowd: Magicon.
[5] COMMUNICATION FROM THE COMMISSION TO THE EUROPEAN PARLIAMENT, THE COUNCIL, THE EUROPEAN ECONOMIC AND SOCIAL COMMITTEE AND THE COMMITTEE OF THE REGIONS Action Plan to enhance preparedness against chemical, biological, radiological and nuclear security risks. COM/2017/0610 final. https://eur-lex.europa.eu/legal-content/en/TXT/?uri=CELEX:52017DC0610
[6] For example see: https://europa.eu/youreurope/citizens/travel/security-and-emergencies/airport-airline-security/index_en.htm
[7] European Commission. EU Science Hub: Europe Media Monitor – NewsBrief https://ec.europa.eu/jrc/en/scientific-tool/europe-media-monitor-newsbrief
[8] There are guidelines available for public consultation by the European Data Protection Board: EDPB 10 July 2019 Guidelines3/2019 on processing of personal data through video devices https://edpb.europa.eu/sites/edpb/files/consultation/edpb_guidelines_201903_videosurveillance.pdf; A publication by the European Union Agency for Fundamental Rights 27 November 2019: Facial Recognition Technology : Fundamental Rights Considerations in the context of Law Enforcement https://fra.europa.eu/en/publication/2019/facial-recognition-technology-fundamental-rights-considerations-context-law
[9] European Data Protection Supervisor. Wojciech Wiewiórowski’s Blog. 21 February 2020. AI and Facial Recognition: Challenges and Opportunities https://edps.europa.eu/press-publications/press-news/blog/ai-and-facial-recognition-challenges-and-opportunities_en
[11] Urban Agenda for the EU. Security in Public Spaces. Orientation Paper. 2 May 2019. https://ec.europa.eu/futurium/en/system/files/ged/orientation_paper_security_in_public_spaces_public.pdf
[13] Commission Recommendation C(2020) 2296 final (of 8.4.2020 ) on a common Union toolbox for the use of technology and data to combat and exit from the COVID-19 crisis, in particular concerning mobile applications and the use of anonymised mobility data. https://ec.europa.eu/info/sites/info/files/recommendation_on_apps_for_contact_tracing_4.pdf
[15] Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation) (Text with EEA relevance) OJ L 119, 4.5.2016, p. 1–88; https://eur-lex.europa.eu/eli/reg/2016/679/oj
[16] Directive (EU) 2016/680 — protecting individuals with regard to the processing of their personal data by police and criminal justice authorities, and on the free movement of such data. https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=LEGISSUM%3A310401_3
[17] Council of Europe, 24 June 2020, Ad Hoc Committee on Artificial Intelligence: ‘The impact of artificial intelligence on human rights, democracy an the rule of law.’ https://rm.coe.int/cahai-2020-06-fin-c-muller-the-impact-of-ai-on-human-rights-democracy-/16809ed6da
[18] European Commission, 18 March 2020, Advisory Committee on Equal Opportunities for Women and Men: ‘Opinion on Artificial Intelligence –opportunities and challenges for gender equality.’ https://ec.europa.eu/info/sites/info/files/aid_development_cooperation_fundamental_rights/opinion_artificial_intelligence_gender_equality_2020_en.pdf
[19] Nemitz, P. (2018). Constitutional democracy and technology in the age of artificial intelligence. Quoted in Council of Europe 2020, see footnote 17
[20] European Commission, 19 February 2020, COM (2020) 65: ‘White Paper On Artificial Intelligence - A European approach to excellence and trust.’ https://ec.europa.eu/info/sites/info/files/commission-white-paper-artificial-intelligence-feb2020_en.pdf
