Terrorism Risk Assessment of Public Spaces for Practitioners
date: 22/04/2020
Applied systematically, terrorism risk assessment provides decision-makers, authorities and public space operators with a method to make informed decisions on the necessary and proportionate security provisions for public spaces, to prioritize and to allocate resources. A comprehensive evaluation of the terrorism risk for a particular public space entails unquantifiable amount of uncertainty and requires the collaboration of different authorities, intelligence services, experts and researchers. In practice, local authorities and security operators may be faced with an overwhelming degree of uncertainty, while they often have to rely on their own judgement and experience for assessing the risk of terrorism.
Our aim here is to review considerations which may be helpful to the security operator or the urban civil servant in the practical terrorism risk assessment for public spaces. We also introduce the EU Vulnerability Assessment Checklist for Public and Security Authorities [1] which is being developed by DG HOME of the European Commission and provides a streamlined tool of elements to be taken into account when assessing terrorism-related vulnerabilities of public spaces. Assessing terrorism risk in a systematic manner is conducive to the implementation of tailor-made solutions for more effective, resource-efficient and proportionate protection.
The Risk Assessment Process
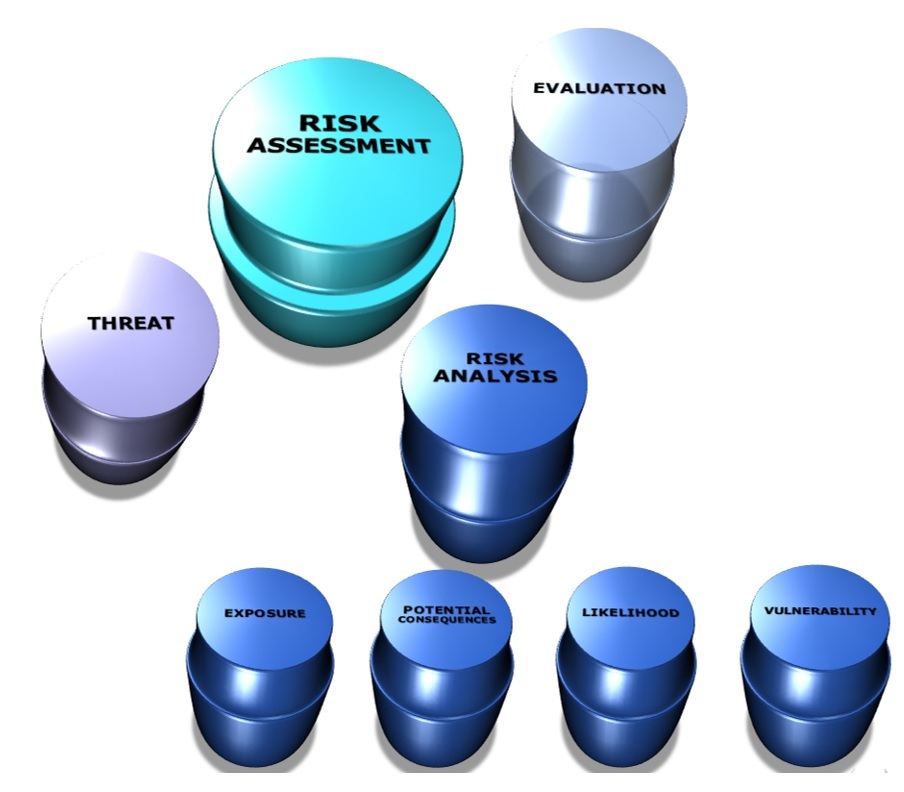
Risk assessment is a continuous process – it must be adapted to new threat levels and modus operandi in function of new technologies and security perceptions. The most common approach for assessing risk [2] is based on three steps:
- Risk identification: Identification of potential terrorist threats
- Risk analysis: Identification of exposed assets (what type of public spaces we are dealing with), analysis of potential consequences, likelihood estimation and identification of vulnerabilities.
- Risk evaluation: Selection of appropriate responses based on the prevailing attack scenarios and their consequences, as were defined in the previous steps.
The European Commission is developing a tailor-made approach addressing terrorism risk (which is a man-made and not natural hazard, and intentional as opposed to accidental), which is particularly intended for use by European urban authorities and security operators.
Threat identification
Evaluating the likelihood of a terrorist attack in general terms and without relying on intelligence information for a particular event is anything but exact science. Some considerations and tools, however, could help in estimating the likelihood and potential modus operandi of a terrorist attack. The figure below presents in blue the considerations which may guide the threat analysis, while the red nuance points to the elements that bring uncertainty.
- Evaluation of political and sociological developments at the international, national and local levels
Terrorist acts are a product of political, ideological, and sociological factors. Consideration of international developments like civil wars, clashes between strong ideologies, conflicts that leave many people exposed to poverty, migration and radicalization is the first step to evaluating the likelihood of a terrorist attack. Such international developments affect the local level when there is military, economic or political positioning by the national government [3] or the presence of diaspora of affected populations. Problematic urban areas with a high concentration of socially marginalized people can provide a breeding ground for terrorism [4].
The causes of the terrorist attacks in Europe in the past few years have been mostly ethno-nationalist/separatist (highest number of attacks, but not the highest consequences in terms of victims and socio-psychological impact), jihadism [5] (the highest number of victims), extreme right or left political ideologies [6]. National security services and Europol [7] issue openly available terrorism trend forecasts, which provide statistics and a general overview of the threat.
Such general analysis and statistics provide a broad perspective on current terrorist trends and set up the context within which local circumstances are to be evaluated. There are also “softer” tools which provide an indication of sociological dynamics which may serve the threat identification analysis. The Europe Media Monitor (EMM) [9] developed by the European Commission, for example, can be used to analyse the use of terrorism related keywords in media and social media channels. Such tools risk to return a lot of “noise” and should be used with the necessary amount of reservation, but they could provide indications on potential terrorist leanings and intentions or the social perceptions associated with the risk terrorism. The Joint Research Centre (JRC) is currently developing a tool for generating terrorism-related statistical data from a broad range of media sources using EMM.
- Past incidents (attacks, foiled or failed events)
Past terrorist attacks can provide indication of terrorist motivation, potential targets and preferred modus operandi. Like other human activities, terrorism is subject to “fashions” and trends. Having an understanding of the tactics employed by aggressors globally could provide a good basis for understanding potential threats locally. Information travels fast and the modus operandi used by attackers at one side of the globe can easily be applied by terrorists at home without necessarily sharing a common goal.
Accessible sources of information related to past terrorist events include:
• The Global Terrorism Database by the University of Maryland [10] is freely accessible but updated on an annual basis, which means that latest data are not readily available.
• Databases by commercial security risk providers like Jane’s (IHS Markit) [11] or Control Risks (Control Risks Group Holdings Ltd, 2019) [12].
• The European Media Monitor (European Commission-EMM) which analyses information from both traditional and social media sources around the globe. The JRC of the European Commission is currently testing the usability of the provided media data via machine learning approaches as a facet of a more comprehensive terrorism threat analysis tool.
Unlike natural hazards, the data from past terrorist events must be used with caution when quantifying terrorist threat [13]. If a city never experienced a terrorist attack, does that mean that there is no likelihood of an attack in the future? If the most recent terrorist attacks were perpetrated with firearms, does that mean that the next one will use the same modus operandi? The presence of radicalized groups in the city can provide an indication of the threat level, but how can security operators and urban decision-makers evaluate the threat of possible “lone-wolf” [14] attacks?
Attempts at quantifying the risk are a stimulating intellectual exercise, but in practice scenario-based qualitative approaches may prove a more effective risk assessment method for a particular public space.
- Attack scenarios for a specific public space at a particular moment or period of time
With the political and contextual background established, the threat identification analysis must focus on the particular attributes of the public space during its everyday use and during its use for a particular event. Having in mind the distinct features of a specific public space, the analysis can be based on attack scenarios considering modus operandi already encountered elsewhere. The EU Vulnerability Assessment Checklist for Public and Security Authorities [15] lists the following attack methods:
- Firearms attacks
- Bladed weapon attack
- Vehicle as weapon attack
- Explosives – carried or concealed
- Explosives – person borne
- Explosives – vehicle (also drone) borne
- Drone as a weapon
- Drone borne agents – CBRN-E
- Chemical agent attack
- Biological agent attack
- Radiological agent attack
The attack scenarios have to be adapted to the changing political, economic, sociological and ideological situation as well as to the availability of new technologies which bring about new threats and new vulnerabilities for our public spaces.
Risk analysis
- Exposed Asset Identification
Public spaces of any nature can be a potential target for terrorist attacks.
But can we treat all our public spaces as a potential target for terrorists? Theoretically, yes, because experience shows that any public place can be a target. But in practice, in order to provide for custom-made proportionate solutions within the limit of resources, we must prioritize through a critical evaluation of each exposed target. Weighing factors to measure the attractiveness of a public place as a possible target to a terrorist attack can be:
- People attendance
- Site symbolism (for example cultural, religious, ideological, historical, economic)
- Size of the facility
- Importance (consequences if the public space is attacked – human life, logistical, economic, social)
- Specific event and presence of VIPs
- Already existing security measures
- Accessibility (free, access control, pedestrian, vehicles etc.)
These weighing factors are subjective. There may be a discrepancy in the interpretation of the criticality of the building/site among operators, who are mainly concerned with functionality and public institutions and policy makers whose focus is public security. It is important that the different views are taken in consideration in order to provide for a balanced, proportionate and effective risk assessment.
- Likelihood of an attack
How likely it is for an attack to take place varies depending on whether the analysis addresses the everyday use of a public space or a particular event. The more “benefit” the target offers to the attacker, the higher the likelihood of an attack. National security services provide terrorism threat level estimates on a national and regional level. Depending on the member state, the likelihood can be categorized as for example,
- rare, unlikely, likely and almost certain
- low, moderate, substantial, severe, critical
The threat level is used as a basis for decisions on protective security measures to be put in place. It is important to keep in mind that, statistically, terrorist attacks are low-probability events.
- Potential consequences
Terrorist attacks are low-probability, but high-consequence events. Clearly the most impactful consequence of terrorist attacks is the loss of human life and the direct physical injuries and psychological traumas suffered by survivors. Immediate economic losses in the destruction of property and infrastructure, disturbed supply chains and increased security costs. In the long term, terrorist attacks shake up stock markets and may negatively impact tourism and foreign direct investments in a country or region. The fear that terrorist attacks engrain leads to loss of trust in institutions and authorities, it provides breeding ground for populism and may ultimately corrugate the moral and social foundations of our societies.
Analysis of the potential consequences of a terrorist attack at a particular public space is important for the proportionality of the employed protective solutions. Past events provide a clear picture for understanding the potential consequences of terrorist attacks.
- Vulnerability Assessment
Vulnerabilities are the inherent weaknesses of a potential target. Critically assessing vulnerabilities in the context of attack scenarios will inform decision-makers on effective deterrence and mitigation measures, strategies to minimize exposure, emergency management plans and enhanced resilience. Vulnerabilities are threat-specific, setting-specific and time-specific.
The EU Vulnerability Assessment Checklist [16] provides a set of factors to consider and practical questions to ask during the vulnerability assessment of different types of public spaces across a broad range of identified threats.
Public space vulnerabilities are categorized according to the different access/entry/exit phases to a public space and are linked to possible attack scenarios and considerations. There are additional vulnerability assessment matrixes for insider threats and drone attacks. The vulnerability aspects to consider are:
- Access roads to venue
- bottlenecks (possible vehicle-borne explosion impact, also for adjacent pedestrian traffic)
- alternative access/exit roads
- proximity to major road infrastructure, residential areas, other transport infrastructure
- access to large/heavy vehicles
- Parking and transport facilities
- Particularities of the entry flows (tunnels, shuttles, narrow lanes)
- Adjacent public places
- Situation of the parking/transport facilities in respect to the public place
- Pedestrian access
- bottlenecks (possible person-borne IED, active shooter incidents)
- Surrounding structures that may be used by terrorists
- Public transport
- Entry / exit points
- crowd conglomeration
- vulnerability to attacks outside the protected perimeter
- emergency exits
- electronically operated equipment (lifts, mobile barriers, etc.)
- Access controls
- Positioning of access controls in a way not causing crowd conglomeration
- Possibility to break through access controls
- Open access public places
- possibility to re-channel the crowd flow
- vulnerability of crowds at entry and exit points outside of the public space
- presence of shelter from a possible shooting/vehicle ramming attack
- protection form drone attacks
- Structural resilience
- Possibility of fragments /structural parts collapsing
- Other buildings/structures in proximity
- Internal security measures
- Means to check / stop attackers
- Control of service staff/vehicles
- Insider threat and internal controls
Systematic and continuous terrorism risk assessment for public spaces is essential for the prioritization, planning and implementation of effective mitigation solutions. In practice, there are no attack-proof solutions and there will always be the acceptable risk factor to weigh in on the decision-making process. Still, the aim of terrorists is to achieve the highest degree of havoc with their attack, thus they would naturally be attracted to exploiting the exposed vulnerabilities of public spaces. The implementation of mitigation measures which address systematically analysed risks will provide increased resilience in case of a terrorist attack and its presence will in itself act as a dissuasion for terrorist targeting.
[1] European Commission (2019), EU Vulnerability Assessment Checklist for Public and Security Authorities, not yet published
[2] International Standards Organization (2018): ISO 31010: 2018 ‘Risk Management – Risk Assessment Techniques’
[3] For example, the Madrid metro bombs attacks in 2004 occurred after Spain sent troops in Iraq.
[4] As the infamous examples of the Molenbeek quarter in Brussels or the Meinau in Strasbourg
[5] Examples are: Paris Charlie Hebdo attack 7 January 2015; Paris attacks 13 November 2015, Brussels bombings 22 March 2016; Nice truck attack 14 July 2016; Berlin Christmas market attack 9 December 2016; Manchester bombing 23 May 2017, Barcelona terror attacks 17 Aug 2017.
[6] Examples are: Munich mass shooting 22 July 2016, Finsbury park car attack 19 June 2019, Halle, Sansony-Anhalt mass shooting of 9 October 2019, Hanau shisha bars mass shootings 19 February 2020.
[7] For example: EUROPOL (2019) European Union Terrorism Situation and Trend Report 2019 https://www.europol.europa.eu/activities-services/main-reports/terrorism-situation-and-trend-report-2019-te-sat
[8] Idem., p.13
[9] European Commission Joint Research Centre (2020) Europe Media Monitor https://emm.newsbrief.eu/overview.html
[10] University of Maryland (2018) Global Terrorism Database https://www.start.umd.edu/gtd/
[11] IHS Markit (2018) Jane’s 360- Defence & Security Intelligence & Analysis https://www.janes.com/
[12] Control Risks Group Holdings Ltd (2018) https://www.controlrisks.com/core
[13] Indeed some analysts go as far as suggesting that probabilistic approach to quantifying terrorist threat can “provide a dangerously misleading foundation for terrorism risk analysis” G.G, Brown, L.A. Cox (2011) ‘How Probabilistic Risk Assessment Can Mislead Terrorism Risk Analysts’, in Risk Analysis, Vol. 31, No. 2, 2011, pp. 196-204, p. 197
[14] These are self-radicalized perpetrators who perform or attempt to perform terrorist attacks after being exposed to propaganda material online. Examples are the far-right inspired massacres in Oslo and then at a summer camp in Utoya, Norway in 2011, the islamist killing of people in Toulouse, France in 2012, the car ramming in Nice in 2016; the stabbing by an islamist in Turku, Finland in 2017 as well as the far-right inspired shooting in Macerata, Italy.
[15] European Commission (2019), EU Vulnerability Assessment Checklist for Public and Security Authorities, not yet published
[16] Idem.
