ICT security in enterprises
Data from December 2022
Planned article update: December 2024
Highlights
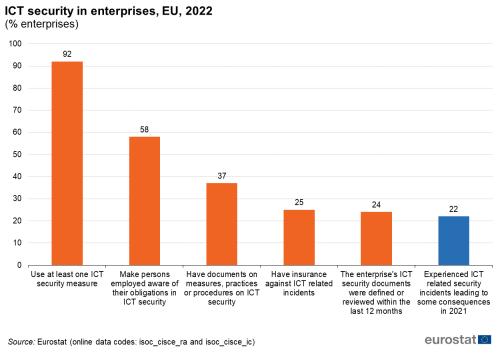
In 2021, 22 % of enterprises in the EU suffered various consequences due to ICT related security incidents.
Source: Eurostat (isoc_cisce_ra) and (isoc_cisce_ic)
This article analyses recent statistical data on information and communication technologies (ICT) security in the European Union (EU). Results were obtained through a specific set of questions in the 2022 questionnaire of the EU survey on ICT usage and e-commerce in enterprises. In this context, ICT security refers to relevant incidents as well as measures, controls and procedures applied by enterprises in order to ensure integrity, confidentiality and availability of their data and ICT systems.
Full article
ICT security in EU enterprises
Source: Eurostat (isoc_cisce_ra) and (isoc_cisce_ic)
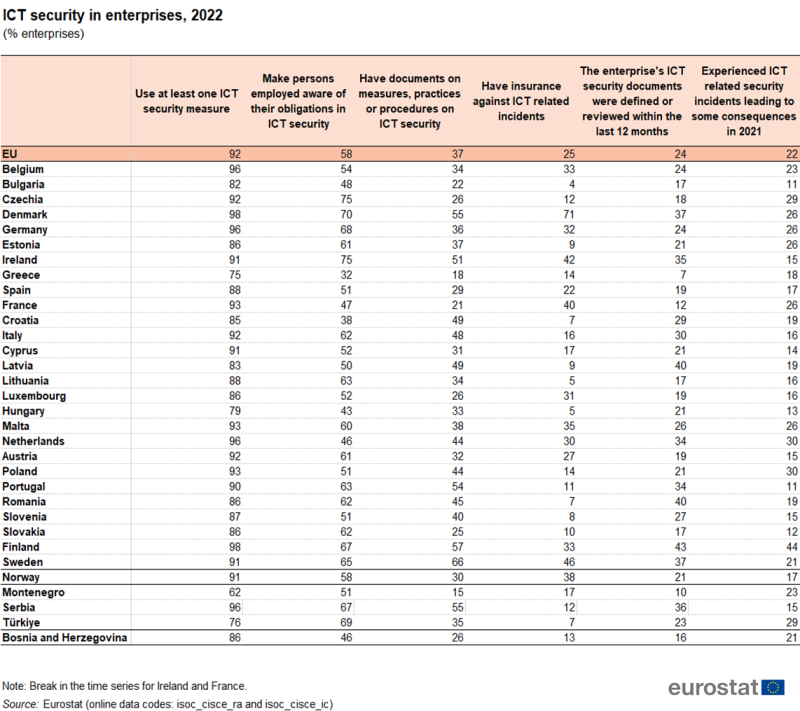
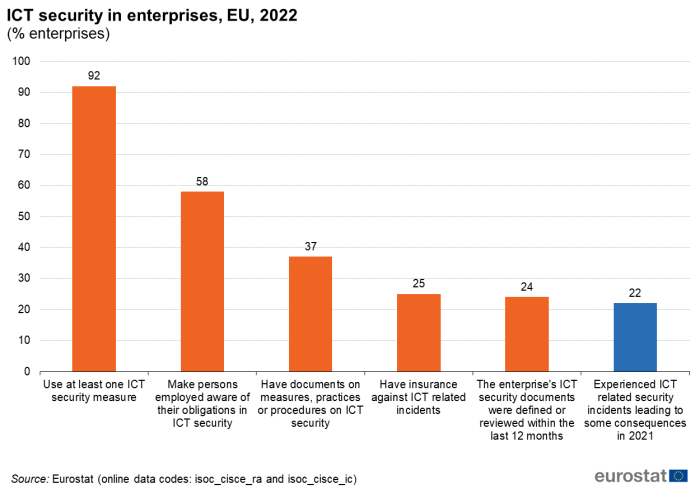
In 2022, 92 % of EU enterprises with 10 or more employees or self-employed persons used at least one measure in order to ensure integrity, availability and confidentiality of data and ICT systems. More than one in three enterprises (37 %) reported having documents putting in place measures, practices or procedures on ICT security. In one in four enterprises (24 %) these documents were defined or reviewed in the last 12 months. Around 58 % of EU enterprises made their staff aware of their obligations in ICT security related issues. One in four enterprises (25 %) was insured against ICT security incidents. Finally, more than one in five enterprises (22 %) experienced consequences due to ICT related security incidents in 2021 (Figure 1).
Source: Eurostat (isoc_cisce_ra) and (isoc_cisce_ic)
ICT security measures
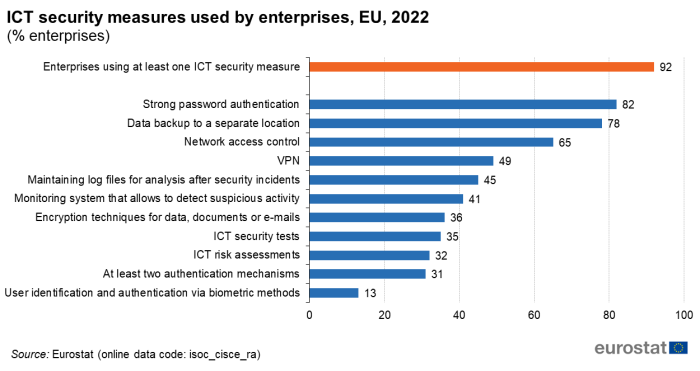
In 2022, 92 % of EU enterprises used at least one ICT security measure. The most common measure used was the strong password authentication (82 %), followed by data backup to a separate location or cloud (78 %) and network access control (65 %). Less than half of enterprises reported using Virtual Private Networks (VPN) (49 %) or maintaining log files for analysis after security incidents (45 %). Enterprises less frequently used encryption techniques for data, documents or e-mails (36 %), ICT security tests (35 %), ICT risk assessments (32 %), a combination of two or more authentication mechanisms (31 %) or user identification and authentication via biometric methods (13 %) (Figure 2).
(% enterprises)
Source: Eurostat (isoc_cisce_ra)
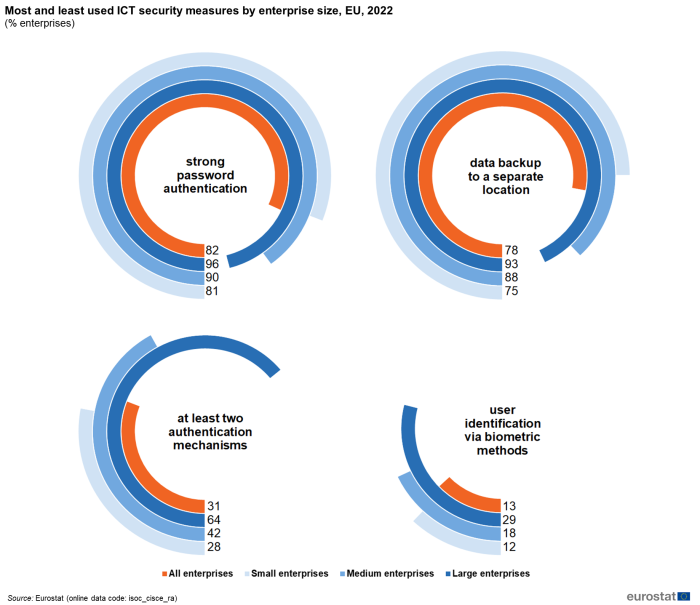
Figure 3 provides a closer look at the most and least used ICT security measures according to the enterprise size. The ICT security measure strong password authentication was used by almost all large enterprises (96 %), by 90 % of medium-sized ones and more than 8 in 10 small enterprises (81 %). Similar figures were reported for the second most popular ICT security measure – the data backup to a separate location, which was used by 93 % of the large enterprises, 88 % of the medium size enterprises and 75 % of small enterprises. Larger differences related to the enterprise size were observed in the share of enterprises using the least common ICT security measures. The authentication by a combination of at least two mechanisms was used by 64 % of large enterprises, while the share of small enterprises using this particular measure was more than two times smaller (28 %). Regardless of the enterprise size, the user identification and authentication via biometric methods was the least used ICT security measure, although the share of large enterprises using this measure (29 %) was significantly higher than the figure recorded for small enterprises (12 %).
(% enterprises)
Source: Eurostat (isoc_cisce_ra)
Documents on measures, practices or procedures on ICT security
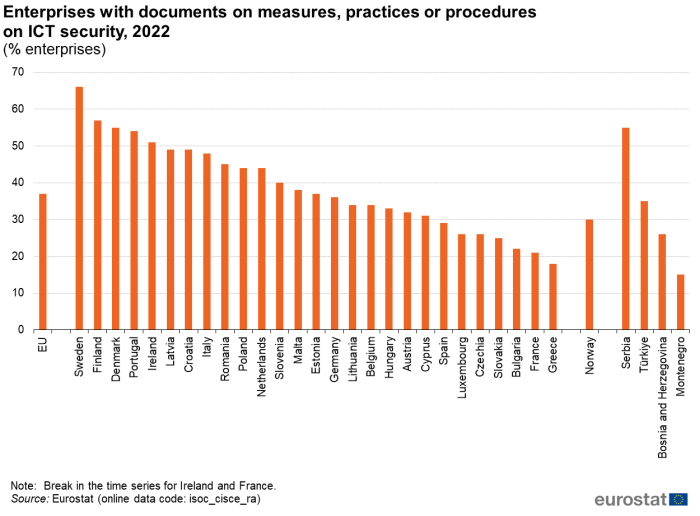
In 2022, 37 % of EU enterprises had documents which put in place measures, practices or procedures on ICT security. Almost two-thirds of enterprises in Sweden (66 %) reported having such documents, while shares higher than 50 % were registered also in Finland (57 %), Denmark (55 %), Portugal (54 %) and Ireland (51 %). On the other hand, less than 25 % of the enterprises had documents on measures, practices or procedures on ICT security in Bulgaria (22 %), France (21 %) and Greece (18 %) (Figure 4).
(% enterprises)
Source: Eurostat (isoc_cisce_ra)
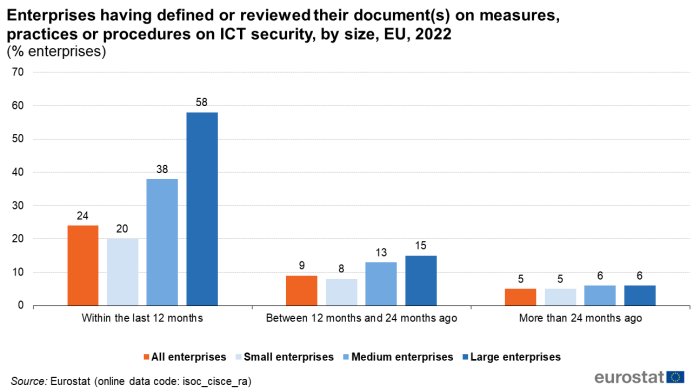
Almost one-quarter of the enterprises (24 %) in the EU have defined or reviewed their documents on measures, practices or procedures on ICT security during the last 12 months. For 9 % this was the case between 12 and 24 months ago and for another 5 % more than 24 months ago. More than half of large enterprises (58 %) reported having defined or reviewed their documents on ICT security within the last 12 months, while for medium-sized and small enterprises this share was significantly lower with 38 % and 20 % respectively (Figure 5).
(% enterprises)
Source: Eurostat (isoc_cisce_ra)
Enterprises make persons employed aware of their obligations in ICT security
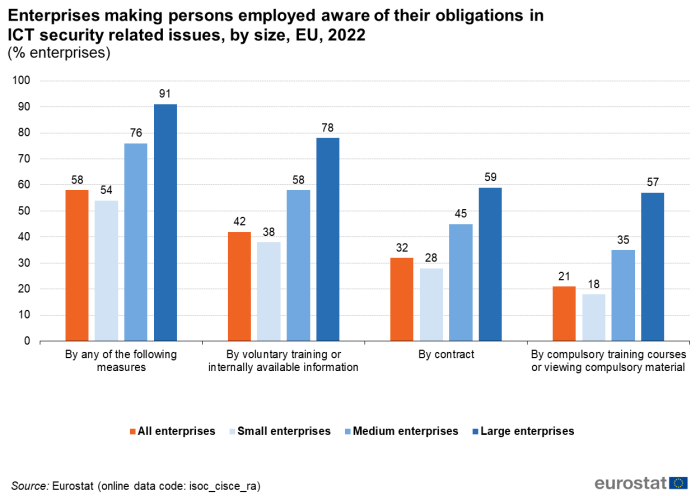
In 2022, almost three out of five EU enterprises (58 %) made their employees aware of their obligations in ICT security related issues. Voluntary training or internally available information for instance on the intranet was the most common form used (42 % of enterprises), followed by contracts such as employment contracts (32 %) and by compulsory training courses or viewing compulsory material (21 %).
The share of enterprises making persons employed aware of their obligations in ICT security by any measure was particularly high for large (91 %) and medium-sized enterprises (76 %). Nevertheless, also more than half of small enterprises (54 %) reported making persons employed aware of their obligations in ICT security (Figure 6).
(% enterprises)
Source: Eurostat (isoc_cisce_ra)
Among all EU Member States, the percentage of enterprises making persons employed aware of their obligation in ICT security ranged from 75 % in both Ireland and Czechia, followed by Denmark (70 %), Germany (68 %) and Finland (67 %), to 38 % in Croatia and 32 % in Greece. In 21 EU Member States, the share of enterprises, which reported making persons employed aware of their obligations in ICT security related issues was higher than 50 % (Figure 7).
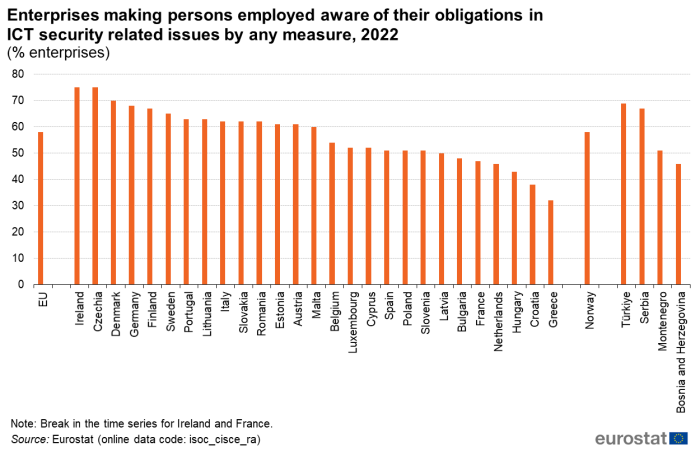
(% enterprises)
Source: Eurostat (isoc_cisce_ra)
In 2022, the majority of EU enterprises (68 %) reported that the ICT security related activities were carried out by external suppliers, while 39 % of the enterprises reported that the ICT security related activities were carried out by own employees. The pattern of relying predominantly on external suppliers for ICT security related activities was valid for both small and medium size enterprises. By contrast, the significant majority of large enterprises (84 %) reported the ICT security related activities being carried out by own employees (Figure 8).
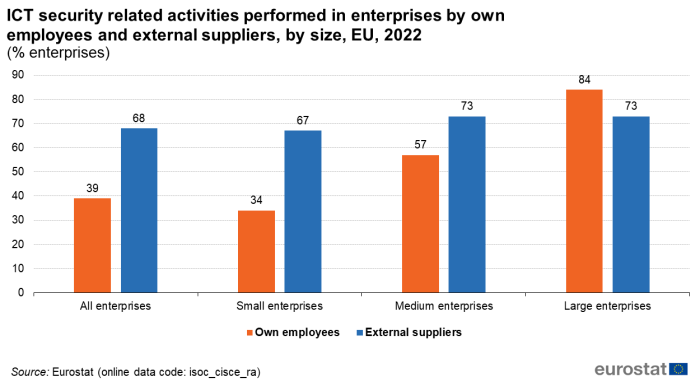
(% enterprises)
Source: Eurostat (isoc_cisce_ra)
The presentation of who performs the ICT security related activities according to the economic activity of the enterprise provides a similar picture. In EU enterprises from almost all sectors, with the exception of information and communication, the ICT security related activities were carried out by external suppliers in 2022. Only in information and communication, majority of enterprises (84 %) reported in 2022 that ICT security related activities were carried out by their own employees (Figure 9).
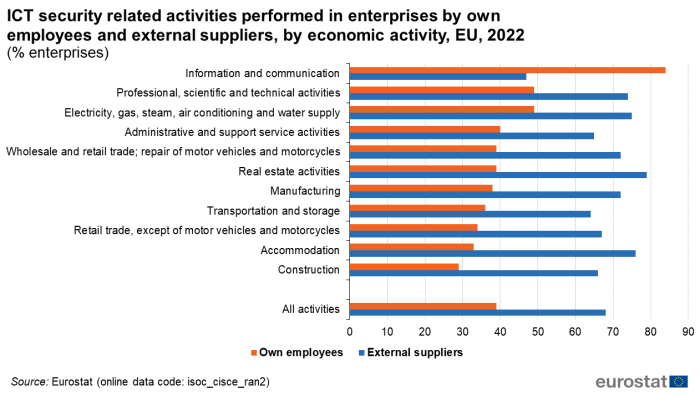
(% enterprises)
Source: Eurostat (isoc_cisce_ra)
In 2021, more than one in five EU enterprises (22 %) experienced ICT related security incidents leading to consequences such as the unavailability of ICT services, destruction or corruption of data or disclosure of confidential data (Figure 10). The ICT security incidents can be caused by malicious attacks from outside or inside the enterprise, or by non-malicious causes, such as hardware or software failures or unintentional action by own employees. In 2021, enterprises more often reported damages to enterprises’ ICT services or data being caused by non-malicious incidents. The most commonly reported consequence caused by ICT security incidents was the unavailability of ICT services due to hardware or software failures (19 % of enterprises). In comparison, unavailability of ICT services due to attack from outside (e.g. ransomware attacks, Denial of Service attacks) was reported by 4 % of enterprises. Destruction or corruption of data resulting from hardware or software failure was reported by 4 % of enterprises, while infection with malicious software or unauthorised intrusion lead to destruction or corruption of data in 2 % of enterprises. Least frequently, enterprises reported disclosure of confidential data due to intrusion, pharming or phishing attack or intentional actions of own employees (1 %) or due to unintentional actions of own employees (1 %) (Figure 10).
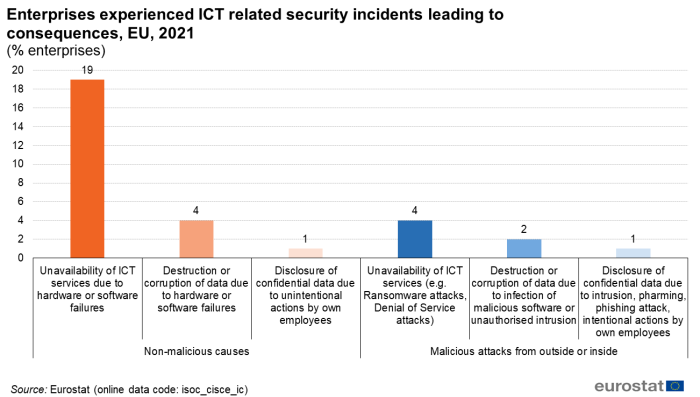
Source: Eurostat (isoc_cisce_ic)
Considering the economic activity breakdown, during 2021, almost one-third of the enterprises in professional, scientific and technical activities and information and communication experienced ICT security incidents leading to unavailability of ICT services, destruction or corruption of data or disclosure of confidential data. In construction and transport and storage this was the case for almost 1 in 5 enterprises (Figure 11).
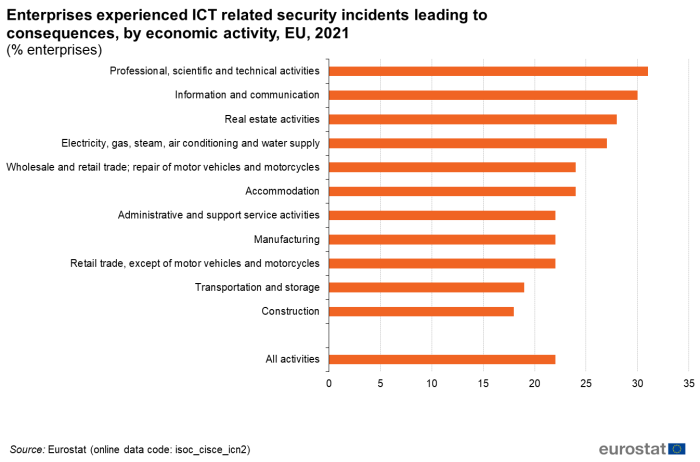
(% enterprises)
Source: Eurostat (isoc_cisce_ic)
Insurance against ICT security incidents
In 2022, 25 % of the enterprises in the EU reported having insurance against ICT security incidents. The highest share was recorded in Denmark, where more than two-thirds of the enterprises (71 %) were insured against ICT security incidents. Furthermore, more than 40 % the enterprises in Sweden (46 %) and Ireland (42 %) reported having insurance against ICT security incidents. By contrast, in Lithuania, Hungary and Bulgaria less than 6 % of the enterprises reported having insurance against ICT security incidents in 2022 (Figure 12).
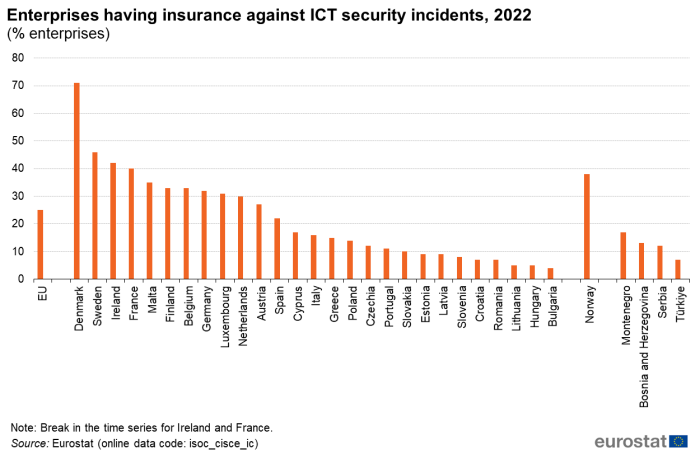
(% enterprises)
Source: Eurostat (isoc_cisce_ic)
The percentage of enterprises that reported being insured against ICT security incidents varied depending on the enterprise size. The share of medium sized enterprises with insurance against ICT security incidents (35 %) was 12 percentage points (pp) higher than among small enterprises (23 %). The highest share of enterprises having insurance against ICT security incidents in 2022 was recorded for large enterprises (45 %)(Figure 13).
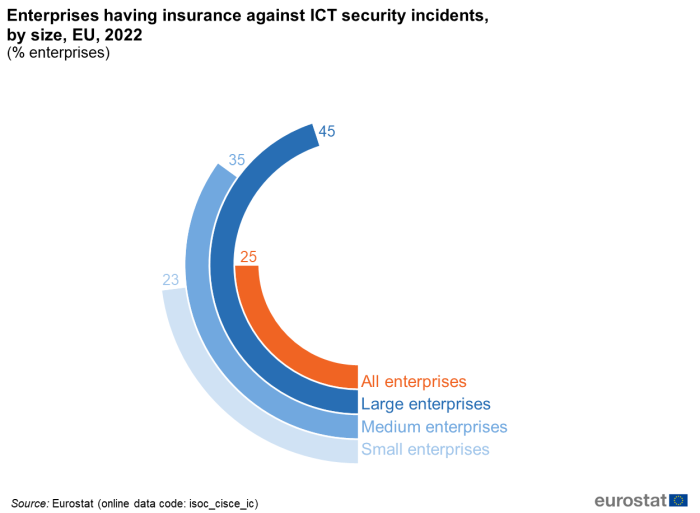
Source: Eurostat (isoc_cisce_ic)
Source data for tables and graphs
Data sources
Source: Data presented in this article are based on the results of the 2022 Community survey on 'ICT usage and e-commerce in enterprises'. Statistics were obtained from surveys in enterprises conducted by National Statistical Authorities in the first months of 2022.
Sample: In 2022, some 150 400 enterprises, with 10 or more employees or self-employed persons, out of 1.47 million in EU were surveyed. Out of these 1.47 million enterprises, approximately 83 % were small enterprises (with 10-49 employees or self-employed persons), 14 % medium (50-249 employees) and 3 % large enterprises (250 or more employees).
Main concepts: The observation statistical unit is the enterprise, as defined in the Regulation 696/1993 of 15 March 1993. The survey covered enterprises with at least 10 persons employed. Economic activities correspond to the classification NACE Revision 2. The sectors covered are manufacturing, electricity, gas and steam, water supply, construction, wholesale and retail trades, repair of motor vehicles and motorcycles, transportation and storage, accommodation and food service activities, information and communication, real estate, professional, scientific and technical activities, administrative and support activities and repair of computers and communication equipment.
Context
In the context of the survey on enterprises, ICT security refers prominently to measures, controls and procedures applied by enterprises in order to ensure integrity, confidentiality and availability of data and ICT systems. The relevant statistics would be used in the context of the European Strategy for Cyber Security that provides the overall strategic framework for the EU initiatives on cybersecurity and cybercrime. Trust and security were a key pillar of the Digital Single Market Strategy and are also an important element of Europe fit for digital age.
From the legislative point of view, on 7th December 2015, the European Parliament and the Council reached an agreement on the Commission's proposed measures to increase online security in the EU. The Network and Information Security (NIS) Directive is the first piece of European legislation on cybersecurity that was adopted by the European Parliament on 6 July 2016 and entered into force in August 2016. NIS includes common provisions across the Union, addressing national capabilities and preparedness, EU-level cooperation, take up of risk management practices and an information sharing culture in NIS and notification of IT incidents. Moreover, on 13th September 2017 the Commission adopted a cybersecurity package. The Cybersecurity Act, which has now entered into force, lies at the core of the package.
Direct access to
- Cloud computing - statistics on the use by enterprises
- ICT specialists - statistics on hard-to-fill vacancies in enterprises
- E-commerce statistics
- E-business integration
- ICT security in enterprises
- Social media - statistics on the use by enterprises
- Digital economy and society statistics - enterprises
- Impact of COVID-19 on the use of ICT in enterprises
- ICT security in enterprises, 2010 - Statistics in focus 7/2011
- Recent Eurostat publications on Digital economy and society
- ICT usage in enterprises (isoc_e)
- ICT security (isoc_cisc)
- Security policy: measures, risks and staff awareness (isoc_cisce_ra)
- Security incidents and consequences (isoc_cisce_ic)
- ICT security (isoc_cisc)
- ICT usage and e-commerce in enterprises (ESMS metadata file — isoc_e_esms)
- Regulation (EU) 2019/2152 of the European Parliament and of the Council of 27 November 2019 on European business statistics
- Regulation (EC) No 808/2004 of the European Parliament and of the Council of 21 April 2004 concerning Community statistics on the information society
- Regulation (EC) No 960/2008 of 30 September 2008 implementing Regulation (EC) No 808/2004 concerning Community statistics on the information society
- Regulation (EC) No 1023/2009 of 29 October 2009 implementing Regulation (EC) No 808/2004 concerning Community statistics on the information society
- Regulation (EU) No 821/2010 of 17 September 2010 implementing Regulation (EC) No 808/2004 concerning Community statistics on the information society
- Regulation (EU) No 937/2011 of 21 September 2011 implementing Regulation (EC) No 808/2004 concerning Community statistics on the information society
- Regulation (EU) No 1083/2012 of 19 November 2012 implementing Regulation (EC) No 808/2004 concerning Community statistics on the information society
- Regulation (EU) No 859/2013 of 5 September 2013 implementing Regulation (EC) No 808/2004 concerning Community statistics on the information society
- Regulation (EU) No 1196/2014 of 30 October 2014 implementing Regulation (EC) No 808/2004 concerning Community statistics on the information society
- Regulation (EU) 2015/2003 of 10 November 2015 implementing Regulation (EC) No 808/2004 concerning Community statistics on the information society
- Regulation (EU) 2016/2015 of 17 November 2016 implementing Regulation (EC) No 808/2004 concerning Community statistics on the information society
- Regulation (EU) 2017/1515 of 31 August 2017 implementing Regulation (EC) No 808/2004 concerning Community statistics on the information society
- Regulation (EU) 2018/1798 of 21 November 2018 implementing Regulation (EC) No 808/2004 of the European Parliament and of the Council concerning Community statistics on the information society for the reference year 2019
- Regulation (EU) 2019/1910 of 7 November 2019 implementing Regulation (EC) No 808/2004 of the European Parliament and of the Council concerning Community statistics on the information society for reference year 2020
- Regulation (EU) 2020/1030 of 15 July 2020 laying down the technical specifications of data requirements for the topic ‘ICT usage and e-commerce’ for the reference year 2021, pursuant to Regulation (EU) 2019/2152 of the European Parliament and of the Council
- Regulation (EU) 2021/1190 of 15 July 2021 laying down the technical specifications of data requirements for the topic ‘ICT usage and e-commerce’ for the reference year 2022 pursuant to Regulation (EU) 2019/2152 of the European Parliament and of the Council