|
|
|
|
|
|
|
|
|
Focus
|

|
|
Use of Digital Technologies for the Protection of Public Spaces
|
- A brief overview of the technologies, which most commonly serve urban authorities and security operators for the protection of public spaces.
-
Tips for choosing the appropriate solutions
- Considerations related to the use of technology for the protection of public spaces.
|
| |
|

|
|

Copyright: Greenbutterfly @adobe.stock The digital revolution has opened up possibilities for gathering and retrieving immense amounts of data in real time. Technologies which used to be confined to specialized forensic laboratories or to critical infrastructures are now more broadly accessible to local authorities and can be applied for improving the day-to-day protection of public spaces. Data from video-surveillance systems, biometric or digital footprint databases and CBRN (chemical, biological, radiological and nuclear) sensors can be analysed and interlinked to produce sense-making information through facial recognition algorithms, artificial intelligence tools and data analytics. Harnessing technological solutions provides plenty of opportunities for enhancing the protection of public spaces. Applied and analysed properly, the data derived from IoT (Internet of things) devices can provide information for early threat detection of multiple scenarios (terrorism, crime, natural disasters, pandemics). The availability of tools to gather more complex, comprehensive and quick information can help better-informed and timelier decision-making. Mobile applications and social media platforms can serve as fora for involving citizens in the protection of public spaces. Better communication channels and integrated systems allow for improved coordination and collaboration among different authorities. These extensive opportunities are matched by equally hefty challenges. In terms of technology, even the best hardware would not be useful without the proper data-analysis software and the trained personnel to handle the information. Different systems must be interoperable if they are to allow for the analysis of data from different sources. Interoperability becomes even a more complex issue if applied to systems used by different authorities, different cities and different countries. Any system must respect the principles of privacy protection enshrined in the General Data Protection Regulation [1]. Technology is a powerful tool for security, but it can be equally powerful as a threat, thus technological protection measures must evolve accordingly. In this article, we will provide a brief overview of the technologies, which most commonly serve urban authorities and security operators for the protection of public spaces. We will provide tips for choosing the appropriate solutions and highlight considerations for the overall management of technological protection systems. The choice of any technological solution applied must be the product of not only the availability of budgetary and personnel resources, but also of a comprehensive risk assessment procedure with informed analysis of the predominant threat and the vulnerabilities for the particular site or event. - Video Surveillance, Sound Detection and Collection of Biometric Data
Biometric data refers to body measurements, which provide individual human characteristics through which a person can be identified. Biometric data includes facial features measurements, iris scanning, voice recognition, fingerprint and palm scans, gait analysis and DNA databases. 
Figure 1: Most common methods for urban authorities and security operators to use biometric data for the protection of public spaces (concept of the authors, icons from http://thenounproject.com)[2] Video surveillance technology has been revolutionized with the introduction of high computing power, huge memory potential and ample processing capabilities. Closed-circuit television (CCTV) systems provide real-time monitoring of large areas allowing for the reduction of patrolling personnel. A video surveillance system usually consists of cameras, transmission media, image analysis equipment, monitors, recording and storage systems. The market offers an overwhelming variety of cameras, which may create difficulties in the choice of the appropriate solution for the particular public space. Among the first considerations in the choice of camera would be the level of detail, the installation point, the desired view and consequently whether it needs to be fixed, equipped with rotating/zooming capacity or multi-lens technology. The quality of the video image does not only depend on the resolution (HD, Full HD, 4K etc.) of the camera, but also on the surrounding lighting, the contrast of the various items relative to the background, the complexity of the environment and the movement of objects or personnel. The choice of the resolution capacity depends on the intended application (detection, face or number plate recognition etc.). Stored images can only be zoomed digitally (in contrast with real-time recordings) so their resolution needs to be high enough to provide crisp and clear results. The operational conditions would also determine the imaging and light sensitivity requirements, as there are visual monochrome and colour cameras, models that can function under night conditions with extremely low light demands (ICCD cameras), and cameras that use thermal sensors and can operate in total darkness (thermal cameras). The transmission of the video signal (analog or digital) to the monitor may have to be broadcasted through buildings, the ground etc., so the hardware to be used (cables, optical fiber, LAN, internet, wireless etc.) needs to be carefully selected to satisfy the video signal quality requirements. Table 1 summarizes the most important characteristics of the surveyed area and the viewing equipment that have to be considered from the decision makers before setting up a video surveillance syste 
Table 1: Video surveillance considerations Sound detection or audio monitoring, when combined with the appropriate software, can automatically filter natural/common noises and distinguish abnormal sounds that are of human (e.g. a scream) or other (e.g. class breaking, gunshots, explosions) origin. Sounds are screened and classified based on their acoustic features and trigger an alarm if they correspond to certain characteristics. The advantage of audio surveillance systems is that they can still operate under low or no light conditions, where video systems may not provide clear images, and they can have a supporting role to images captured by a CCTV, providing additional verification in case of an incident. The effectiveness of such systems is lower in noisy environments with multiple sound sources, as they have to separate background noise from the alarm-triggering sounds. With the advent of machine learning techniques, the identification of threat sounds (e.g. gunshots) has become more accurate thus reducing false alarms. Moreover, the distribution of multiple sensors in city areas also allows the identification of the event location thus allowing targeted law enforcement actions. Other biometric identification methods, like iris scans, fingerprints and palm identification can be used for access control of authorized personnel in buildings. These technologies provide a simpler (in terms of the volume of algorithm input) and not so easily alterable method for identification. The major drawback of these technologies is that a database with the biometric data of all authorized personnel must be kept by the security services and be accessible by the control device, which creates risk for hacking the database with malicious intentions. Such systems can also be more cumbersome than conventional solutions like badge readers or pin code-based access authorizations. Video surveillance and sound detection technologies are not flawless. They can pose technical problems like lack of accuracy (for example, blurred image, bad quality sound or false alarm due to noise pollution) or blind spots in coverage. If the system was created in different phases, there may be discrepancy in the formats of the footage different video cameras are producing, which would hamper the analysis. It is important to provide for regular preventive and corrective maintenance of the hardware and update of the analysis software. Lack of ample data storage, proper filing plan and defined procedures for retaining and archiving of footage files can cause loss of data or delays in the data analysis. Another major drawback is that video surveillance cameras accumulate immense amounts of footage [3] which has to be thoroughly analysed by security operators if an incident is to be prevented or meticulously sieved through in case an incident materializes. 
Figure 2: The immense amounts of data surveillance technology generates, can hinder its analysis and thus render it futile (concept of the authors, icons from [4]) Even if the accessibility to substances required for creating Chemical, Biological, Radiological, Nuclear and Explosives (CBRN-E) agents or devices is usually limited, terrorists might still be able to possess them, enabling them to perform an attack. To facilitate better understanding and improved cooperation between Member States, the European Commission issued a dedicated Action Plan [5] that proposes several actions to contribute to the preparedness and resilience in case of a CBRN-E attack. Sensors detecting CBRN-E threats, that includes more than one thousand agents, used to be the domain of secret services and highly specialized personnel. In the last years more accessible technologies allow for almost real-time detection by trained security operators. Various technologies can be employed for detecting the presence of dangerous agents: for example, ion spectrometry for tracing chemicals and explosives, gamma-ray spectrometry for radiological agents or polymerase chain reaction assays for detecting biological threats. Such technologies are extensively used in the civil aviation field to identify the unique attributes and chemical components of CBRN-E agents (focusing mainly on detection of explosives and weapons). X-ray scanners, which use computerized tomography, can detect explosives hidden in bags or suitcases, but they have their drawbacks especially in the face of improvised explosive devices or mouldable plastic explosives, the shape of which cannot be easily recognized through an X-ray scan. The market offers equipment which can detect the majority of hazardous agents. Selecting an appropriate sensor depends on the established attack scenario and the relevant risk analysis. Attacks with the use of CBRN agents are of low probability but could potentially have a great societal impact. The detection of an ample range of agents may require the use of multiple systems that have to work together through a dedicated interface, which may increase operational complexity. The optimal and accurate sensor placement following a detailed study on the facility’s needs is essential for minimizing their number (combination of protected area and sensor coverage range) and keeping low the initial, operational and maintenance costs. Access control systems serve to block the entry of unauthorized or suspicious individuals or threatening objects to public or private spaces. Badge readers are commonly used to control entering personnel by validating identity data saved on a chip on the card through magnetic stripe or proximity reader. Touchpads requiring a code or biometric scanners (fingerprint or retina) can also be used for access control. Often, usually at crowded events or public buildings, metal detectors are used for checking of unauthorized metal objects, but they may have the drawback that they are not sensitive towards non-metallic weapons. Full-body scanners (millimetre-wave or X-ray) can detect also non-metallic objects concealed on a person’s body, but have the disadvantage of significantly slowing down the flow of people and of being relatively expensive. Full-body scanners are strictly regulated by EU regulations and must meet operational requirements and detection performance standards [6]. To ensure that access to restricted areas is prohibited, various intrusion detection systems may be used, such as glass break sensors, laser scanners, motion and radar detectors, magnetic contacts, pressure-sensitive mats, trip wire sensors and volumetric surveillance sensors. - Internet of Things, data from smart city sensors
Our cities are interweaved with sensors from public transportation and road traffic networks, energy, communication or transactional infrastructure, civil security and law enforcement agencies, public interest networks and myriad of other services. The Internet of Things concept refers to the computing devices embedded in everyday objects, which can send and receive data. These sensors generate huge amounts of data referred to as “big data”. Urban security can profit from information produced by these sensors. Knowing where the traffic is blocked in a city, or the hours and zones in which traffic is at its peak could provide decision makers with a good basis for the vulnerability assessment of assets during varying traffic conditions. Unified security systems deal with complex and diverse data from video surveillance, licence plate recognition and access control tools that is mixed with data from traffic lights, traffic or communication sensors providing a very good overall picture of incidents in real time. Unifying the numerous sensors and data sources in public spaces opens up the way for seamless data-sharing and more collaboration among different authorities and security providers. The smart city concept model is laid out in ISO/IEC 30182:2017 “Guidance for establishing a model for data interoperability” based on the alignment of ontologies used in the data emitted by different sensors. Using the potential of this fast-growing field requires decisions on the software tools, hardware platforms and data protocols in order to ensure efficient data access and sharing. Without sharing, “big data” cannot work – its potential is harnessed only when it is “big”, but sharing data in the field of security will have to be done through strictly defined secured channels and protocols. The tools for anonymizing such data without rendering it useless for security purposes is also an ongoing debate which will have to be resolved for the benefits big data offers when used at its full potential. - Real-time data mining and data analytics
Thankfully, the revolution in hardware tools has been paralleled by significant developments in technologies for analysing the data obtained by video surveillance cameras, sound detection devices or Internet of Things (IoT) sensors. 
Figure 3: Making sense of data through data-analytics techniques Data-mining refers to uncovering trends or patterns in big chunks of data, while real-time is the capacity to provide the crunching of data instantaneously. Text mining, for example, is a data-mining technique, which allows for the processing of huge amounts of text and aggregate it into trend patterns according to the users’ needs. The Europe Media Monitor [7], for example analyses both traditional and social media aggregating data from 300,000 news articles per day from world-wide news portals in up to 70 languages. The Joint Research Centre of the European Commission is developing an open-source tool which analyses terrorism incident data collected by the Europe Media Monitor which are useful in assessing emerging threats and terrorism tactics. Data-analytics is about extracting, cleaning, transforming, modelling and visualizing the data and converting it to meaningful information or hypotheses deemed useful to decision makers. The output of data analytics can be descriptive (what happened), diagnostic (why it happened), predictive (what might happen) and prescriptive (recommend action based on the forecast). The capacity of video-surveillance systems is not only due to the broad availability of hardware, but also due to the elaborate software solutions which can be applied to analyse the data collected. Such systems are widely used to automatically recognize vehicle number plates that enter into restricted access zones (e.g. in historic city centres), for speed checks and police enforcement purposes. The algorithms used for security checks can be divided in three categories serving different objectives as shown in Table 2. 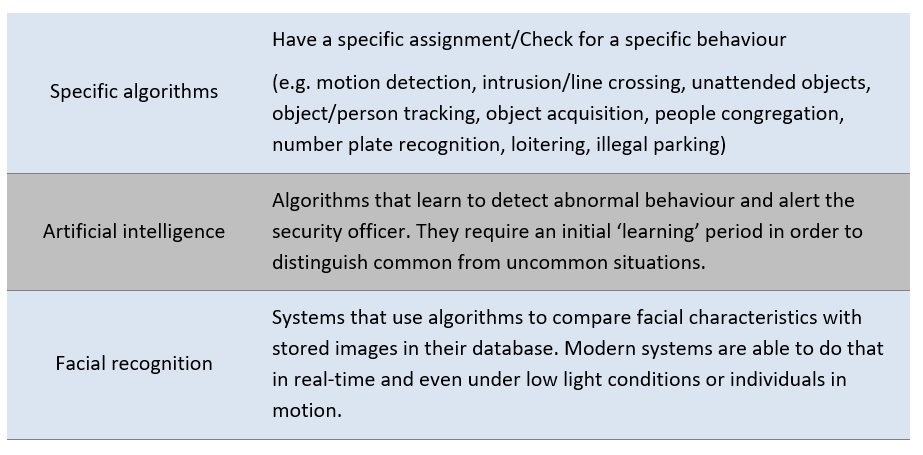
Table 2. Video analysis algorithm types. For the purposes of protecting public spaces, facial recognition can facilitate the identification of suspicious individuals in a crowd by comparing real-time images sent by surveillance cameras with a database of images of potential perpetrators. More advanced technologies can incorporate facial recognition algorithms with other biometric data like gestures, gait, body mass or with personal objects (watch, handbag, jewellery) for higher precision in the identification. New artificial intelligence (AI)-based analytics software can help in reducing the effort of constantly monitoring real-time video footage. Such systems can, for example, identify non-standard situations (e.g. people gathering), perform geofencing (i.e. control whether somebody is trespassing certain restricted areas) or identify objects and unattended luggage. Facial recognition technologies have stirred up a lot of controversy. There is no consensus in the EU on how to apply GDPR concepts as data minimisation, accountability and transparency of AI systems [8]. The machine learning algorithms feeding artificial intelligence systems get “trained” with data from previous incidents or arrests. Such data may be biased, making the algorithm biased thus triggering biased decision making towards particular ethnic or religious groups. The European Data Protection Supervisor favours the use of the precautionary principle and a moratorium on the use of facial recognition technologies until their impact on society and individual freedoms are clarified and regulated [9]. Big data analytics refers to the systematic extraction of information from huge, often heterogeneous data sets. It is the way to convert all the data from smart city sensors and the Internet of Things to sense making information. Big data analytics is a highly dynamic field, where significant improvements in available technologies are announced daily. The field faces significant challenges like problems of interoperability (how to compare data from different sources measured in different time lapses and using disparate metrics), accessiblity (who has access to the data), accountability (how was the data analysed in order to arrive to certain information), storage (not only the size but also the geographical location of the servers, how long is the data to be retained), cyber-security (how to protect the data and the outputs from hackers), and, definitely not least, compliance with the GDPR. Smart City platforms offer the environment for data collection from city sensors and the possibility to integrate with urban intelligence analysis. As an example, FIWARE [10] is an open source cloud platform developed under the initiative of the European Commission in order to provide a space for small and medium size enterprises to make full use of the potential presented by the growth of smart city data and interconnectivity. Such system allows for the integration of heterogeneous devices and sensor networks and the coordination of different systems. The core of such system, the EC connective Europe facility (CEF) Context Broker, is designed to allow the management and sharing of contextual data in real-time. Some examples include Smart Security scenarios with the integration of video streams analytics. However, the convergence of Smart City systems and Security/Surveillance systems is usually challenging because of different roles and information confidentiality of the city management and law enforcement departments. - Mobile phone applications
Mobile phone applications may allow for the participation of citizens to the protection of public spaces. As the Urban Agenda orientation paper [11] states: ‘An integrated approach to safety has at its heart the local social stakeholders, valuing their contribution in terms of both understanding of local needs and sharing of responsibilities related to the care of the places and relations. The involvement of local people and social players in fact strengthens the sense of «presence» of the community in the local area, recognizing the role of protection and support of the perception of greater safety.’ Under the Horizon2020 programme [12], the European Commission has funded several projects to develop mobile phone applications in the field of security. The experience from the COVID-19 related mobile phone applications brings about lessons that can be applicable to the protection of public spaces. The effectiveness of such applications depends on various factors: the number of users they attract, the trust of the users that their data will be protected and used only as agreed, the ability of authorities to use the data generated by such applications in their decision-making, integration and data sharing with other systems and applications, cross-border and cross-regional interoperability with other systems [13]. Experience shows that if such applications are to be effective they have to be developed including different stakeholders: security operators, urban authorities, data protection authorities, experts and researchers, the private sector, citizens groups. The European Commission has recommended [14] the development of a Toolbox of digital means to address the COVID-19 crisis. The Toolbox will be based on a pan-European approach for the use of mobile applications coordinated at EU level and on a common scheme for using anonymized and aggregated data. Similar levels of cooperation and coordination at EU level are necessary if mobile apps for the protection of public spaces are to be effective. Any technology collecting data related to EU citizens must respect the EU General Data Protection Regulation (GDPR) [15], which harmonizes data privacy laws across the EU with the aim of protecting EU citizens from privacy and data breaches. The GDPR applies to the processing of personal data by controllers and processors in the EU, the processing of personal data of data subjects and the monitoring of behaviour that takes place within the EU. It establishes the rights of data subjects defining rules on granting and withdrawing consent to use persona data, the right to access users’ personal data and the way it is being used, the right to be forgotten (i.e. to request erasure of personal data), ability to use data collected by one controller for another controller (data portability). The GDPR establishes the concept of privacy by design, which means that a controller collects and retains only the data which is absolutely necessary for the performance of its duties (data minimization and proportionality) and limits the access to personal data to those processing it (data anonymization). Another directive which is relevant to the use of technologies for the protection of public spaces is the EU Directive for the protection of personal data processed for the purpose of criminal law enforcement [16] which applies the principles of the GDPR to the specificities of law enforcement needs. The main objectives of the directive are to better protect individuals’ personal data when it is processed by police and criminal justice authorities and to improve cooperation in the fight against terrorism and cross-border crime in the EU by enabling exchange of information between police and criminal justice authorities (both in terms of national and cross-border cooperation). Compliance to the directive includes the designation of a data protection officer to help the competent authorities ensure compliance with the data protection rules as well as the requirement to carry out an assessment of potential impact where a type of processing has a high risk of breaching an individual’s privacy. Despite the adoption of the GDPR and the Directive for the protection of law enforcement data, national legislations and local level practices across the EU diverge. The rapid development of technologies which can be employed in the field of protection of public spaces requires continuous re-examination of the application of GDPR principles and what they mean precisely for a given technology or tool. Such considerations can be thoroughly developed only through an open debate among all relevant stakeholders. The use of surveillance technologies may have a “chilling” psychological effect, where people may feel inclined to adapt their behaviour to a norm and this shifts the balance of power between the individual and the state or the organization using surveillance [17]. That means that even if the use of the technology is in full respect of the GDPR, its use may still be intrusive of citizens freedoms and integrity. A well-observed problem is the bias of AI systems – for example algorithms which are trained on data from men or Caucasians leading to broader error margin for women or individuals of different race, also algorithms bear the biases of their developers and cannot be completely neutral [18]. There are calls for designing and creating security technologies with human rights, democracy and rule of law taken in consideration from the outset of the project – the so called “Human Rights, Democracy and Rule of Law by design” [19] underpinned by an obligation to perform Human Rights, Democracy and Rule of Law Impact Assessment before deploying the technology. AI is subject to the same laws governing all other technologies, but some specific characteristics of AI technologies make them more elusive to legal evaluation – for example their opacity (the so called “black-box effect”), complexity, unpredictability and partially autonomous behaviour [20]. In its White Paper on Artificial Intelligence [21], the Commission proposes a risk-based approach to evaluate the need for modifying existing regulations to address the challenges posed by artificial intelligence based technologies. It is likely that technologies used for the protection of public spaces would more often than not fall under the high-risk category. The White Paper states that a broad European debate will be launched to gather and address societal concerns to the use of AI in public places. - Protecting the technologies for protection of public spaces
Data, its collection and its analysis, is at the bottom of the technological revolution. The problem with the use of personal data is that once breached, it is difficult (not to say impossible) to rectify. As the trend is to use more and more technological solutions by different actors for the protection of public spaces, this would bring about new vulnerabilities with perpetrators exploiting the weak spots of such technologies. On the one hand, the problem with small-scale autonomous technological systems is that they cannot afford state-of-the-art levels of protection and that they are also probably less efficient as the power of technological solutions lies in the large amounts of data. On the other hand, interconnectedness of different systems in a large-scale security set-up can bring about cascading failures with quick and unpredictable consequences and further reaching ramifications in case of a hacking attack. Any technological solution applied for the protection of public spaces must integrate security at every stage of the development of the tool. Tools which may be secure when operating in isolation may present vulnerabilities when connected to other systems. There must be continuous risk management of the systems in line with other technological tools employed both within and outside of the organization. Technology offers a broad range of opportunities for the protection of public spaces. Technological solutions can assist the prevention of terrorist attacks, can substantially decrease the reaction response time to threats and incidents, can provide for better informed decision-making and increased cooperation, coordination and sharing of data among stakeholders, authorities and Member States. Still, digital technologies cannot serve as a panacea which would cure all issues related to the protection of public spaces. They have to be developed in concordance and integrate with physical protection measures. Technological solutions and their use must be designed to respect privacy regulations. Security operators and urban authorities must be aware of the potential vulnerabilities technological solutions open up and to apply systematic risk assessment, security and maintenance procedures. Accountability, transparency and reliability in operating security technologies are the foundations for public trust. Ultimately, the trust of the citizens is the foundation upon which the effectiveness of technological solutions for the protection of public spaces can be constructed. [1] Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation) (Text with EEA relevance) OJ L 119, 4.5.2016, p. 1–88; https://eur-lex.europa.eu/eli/reg/2016/679/oj [2] Icons from The Noun Project https://thenounproject.com as follows: from bottom left clockwise: Voice recognition: Gregor Cresnar; Fingerprint: Eucalyp, Facial Recognition: Vectors Point, Security camera: bmijnlieff ; Iris scan: Nociconist, Crowd: Magicon. [3] Just to mention one example: After the terrorist bombing of a concert hall in Manchester in 2017, British police had to wade through more than 16,000 hours of CCTV footage. Source: - The Economist. ‘Walls have eyes Street-level surveillance is everywhere.’ Technology Quarterly Jun 2nd 2018 https://www.economist.com/technology-quarterly/2018-05-02/justice [4] Icons from The Noun Project https://thenounproject.com as follows: from bottom left clockwise: Voice recognition: Gregor Cresnar; Fingerprint: Eucalyp, Facial Recognition: Vectors Point, Security camera: bmijnlieff ; Iris scan: Nociconist, Crowd: Magicon. [5] COMMUNICATION FROM THE COMMISSION TO THE EUROPEAN PARLIAMENT, THE COUNCIL, THE EUROPEAN ECONOMIC AND SOCIAL COMMITTEE AND THE COMMITTEE OF THE REGIONS Action Plan to enhance preparedness against chemical, biological, radiological and nuclear security risks. COM/2017/0610 final. https://eur-lex.europa.eu/legal-content/en/TXT/?uri=CELEX:52017DC0610 [12] Call for proposals for fight against crime and terrorism H2020-FCT-2014 [15] Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation) (Text with EEA relevance) OJ L 119, 4.5.2016, p. 1–88; https://eur-lex.europa.eu/eli/reg/2016/679/oj [19] Nemitz, P. (2018). Constitutional democracy and technology in the age of artificial intelligence. Quoted in Council of Europe 2020, see footnote 17 |

|
|
|
|
|
|
Upcoming events
|

|
|
EU Digital Autumn School on the Protection of Public Spaces
|

|
 |
 |
|
Date |
|
01/10/2020 - 04/11/2020
|
|
 |
 |
|
Venue |
|
Online via Zoom, 5 sessions, 2 hours each
|
|
 |
 |
|
Organiser |
|
European Commission
|
|
|
|
|
|
|
|
|
|
|
News from the EU
|

|
|
The EU Security Union Strategy
|
|
On the 24 July 2020, the European Commission set out the new EU Security Union Strategy for the period 2020 to 2025, focusing on priority areas where the EU can bring value to support Member States in fostering security for all those living in Europe.
|
|
|

|
|
On the 24 July 2020, the European Commission set out the new EU Security Union Strategy for the period 2020 to 2025, focusing on priority areas where the EU can bring value to support Member States in fostering security for all those living in Europe. From combatting terrorism and organised crime, to preventing and detecting hybrid threats and increasing the resilience of our critical infrastructure, to promoting cybersecurity and fostering research and innovation, the strategy lays out the tools and measures to be developed over the next 5 years to ensure security in our physical and digital environment. The new Security Union Strategy is built around the following objectives: - To build capabilities and capacities for early detection, prevention and rapid response to security crisis
- To focus on results
- To link all players in the public and private sectors in a common effort.
The document defines 4 strategic priorities and corresponding actions as described below : 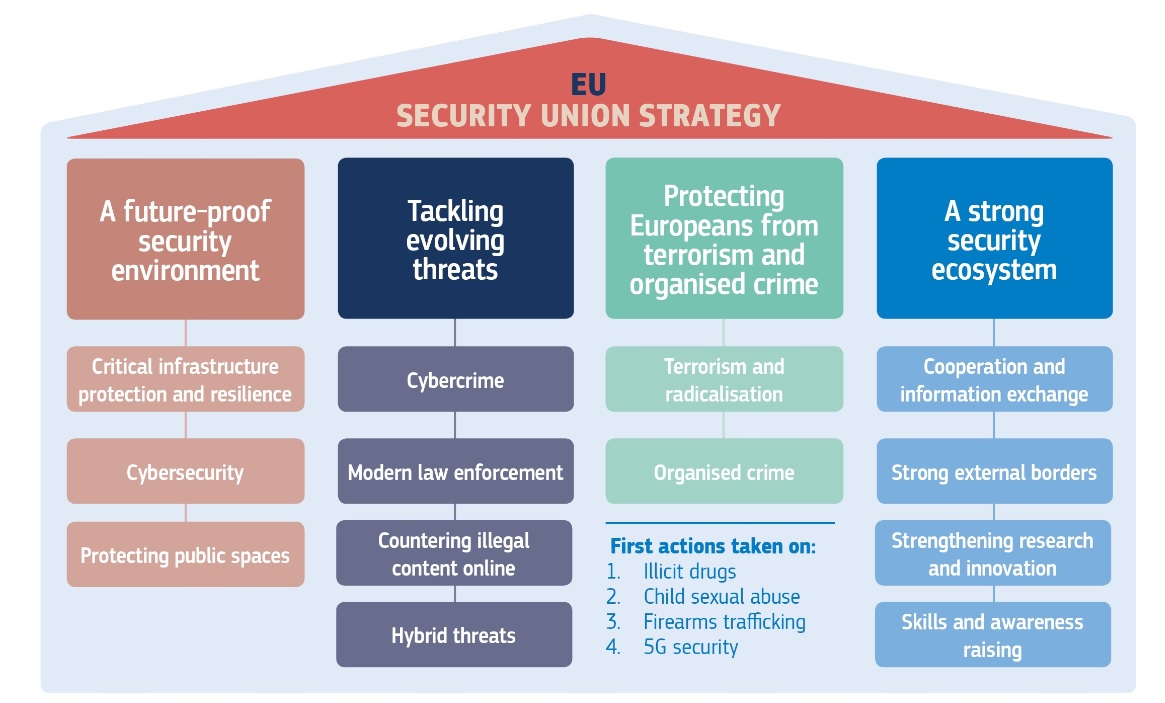
From a Counter-Terrorism perspective, this strategy includes current and future actions: - To adapt the EU’s existing framework to better protect critical infrastructures and to build new tools to support their resilience;
- To update the European Cybersecurity strategy;
- In light of the recent terrorist attacks and with the rise of extremism, the strategy stresses the importance of protecting public spaces (including places of worship and transport hubs). It notably covers physical protection, adequate detection systems, guidance and recommendations. Awareness raising, performance requirements and testing of detection equipment and enhancing background checks to address insider threats will also be part of the approach;
- To continue to develop actions (common testing methodology, information sharing, guidance and good practice) to counter the misuse of drones;
- To enhance law enforcement capacity in digital investigations: common approach on Artificial intelligence, cross-border access to electronic evidence for criminal investigations (proposals still pending agreement by the European Parliament and Council), access to digital evidence, encrypted information;
- To support and develop measures to counter threats from CBRN agents and home-made explosives;
- Regarding the threat posed by Foreign Terrorist Fighters, the implementation of border security legislation and the full use of all relevant EU databases to share information on known suspects are key steps;
- To modernise the EU legal framework for law enforcement cooperation through the creation of an EU “police cooperation code”, streamlining the different outdated EU instruments of operational law enforcement cooperation (in particular cross-border police cooperation), improving Europol’s mandate.
Following up to this security strategy, the next strategic policy document on Counter-Terrorism will be a new Counter-Terrorism Agenda for the EU in 2021.
|

|
|

|

|
|
A new call for proposals focusing on the protection of public spaces with focus on places of worship, vulnerability assessment, detection dogs
|
|
The Commission has published a new call for proposals for € 12 million under the Internal Security Fund-Police to fund projects improving the protection of public spaces in line with the EU Action Plan to support the protection of public spaces.
|
|
|

|
|
The Commission has published a new call for proposals for € 12 million under the Internal Security Fund-Police to fund projects improving the protection of public spaces in line with the EU Action Plan to support the protection of public spaces. Project proposals submitted under the call must address at least one of the following priorities: - Enhance the protection of places of worship,
- Develop and implement the good practices listed in the Commission Staff Working Document “Good practices to support the protection of public spaces” in the areas of vulnerability assessments and planning, awareness and training, physical protection and coordination and cooperation between public and private stakeholders,
- Strengthen the detection of threats by detection dogs in public areas.
The following entities can apply as lead applicants or co-applicants: • public bodies; • non-profit-making private entities; • profit-making entities. Deadline for applications: 24 September 2020 – 17:00 Brussels For further information and proposal submissions please visit the EU Funding & tender opportunities portal.
|

|
|
|
|
|
|

|

|
|
Publication of a dedicated call for proposals on testing countermeasures against unmanned aerial systems (UAS)
|
|
In order to support the execution of the Programme, DG HOME has issued a call for proposals to fund work aimed at enhancing European coordination between Member States in countermeasures testing.
|
|
|

|
|
Following consultations with the Member States in recent months, DG HOME has now established the European Programme for counter-UAS systems testing, which is intended to facilitate a more common European approach to the testing of UAS countermeasures for use in Europe. In order to support the execution of the Programme, DG HOME has issued a call for proposals to fund work aimed at enhancing European coordination between Member States in countermeasures testing. The call, which is funded through the Internal Security Fund-Police (ISF-Police) is worth € 3.5 million. The ultimate aim of work funded through the call is to provide the Member States with a more common baseline understanding concerning the effectiveness of different commercially available counter-UAS solutions. More information about the call can be found here. The deadline for proposals is 14 October 2020.
|

|
|
|
|
|
|

|

|
|
Numerical simulations for the performance assessment of vehicle security barriers
|
|
Report from the Workshop organized by the Joint Research Centre of the European Commission on Numerical simulations for the performance assessment of vehicle security barriers
|
|
|

|
|
Terrorist attacks on public spaces employing vehicle ramming as modus operandi have become recurrent in Europe in the last years. The attacks in Nice and Berlin in 2016 or Barcelona and London in 2017 constitute sad demonstrations of the impact such attacks can have - in terms of loss of human lives, physical and psychological injuries, economic losses and longer-term sociological repercussions. These so-called vehicle-as-a-weapon attacks comprise of a speeding vehicle (a car or a truck) that rams into a crowded pedestrian area, like city centres or open-air events. Vehicle security barriers preventing the entry of vehicles into pedestrian zones can be an effective mitigation measure against vehicle-ramming attacks [1]. They can take various forms like bollards, wedge barriers, beam barriers, concrete Jersey barriers, concrete sitting benches, flower planters or other architectural elements that can be harmonically incorporated with the aesthetics of the surrounding public space. 
Examples of vehicle security barriers [1] To serve as an effective mitigation solution, vehicle security barriers must be carefully manufactured, designed and installed to accomplish various tasks, such as for instance preventing heavy-duty incoming trucks at high velocity from breaking through or narrow vehicles to squeeze in between them and access the protected area. Currently, the performance of barriers against vehicle impact is certified through physical tests using full-scale vehicles. This testing method guarantees that all complex phenomena during the vehicle impact test are taken into account, but due to the high cost only a limited number of impact scenarios is assessed (usually only one). The harmonisation of vehicle barrier testing standards across the EU will ensure common performance and safety levels [2] and will enhance the single market for security products. Harmonization can be assisted through the use of numerical methods. Numerical simulations are cost-efficient and can be used to assess different impact scenarios (changing the vehicle’s velocity, its type or its angle of impact). Numerical testing methods will also open the way to creativity and the development of innovative protective structures which are integrated to the urban aesthetics and cultural character of the surrounding area. Guidelines for the use of numerical tools can be placed at the disposal of urban authorities and security operators for the assessment of ad-hoc security solutions. State-of-the-art numerical techniques have been vastly used in the automotive industry for assessing the crashworthiness of vehicles under different impact scenarios. Numerical testing has allowed for a significant reduction in the costs of experimental campaigns without sacrificing the desired accuracy in the performance of the products under various impact loading scenarios. Similar numerical techniques can be employed to study the behaviour of security barriers under vehicle impact. 
Examples of numerical simulations [3] What is still missing in exploiting the potential of numerical tools in the testing of vehicle barriers are generic harmonized numerical models for various vehicle classes independent from the characteristics of the commercial brand. Such general vehicle models will be made available to the relevant stakeholders for the development of numerical techniques which will serve as a basis for harmonization and eventual standardization. The first step in this process is to determine the needed level of detail for each vehicle class. 
Examples of vehicle classes [4] To this end, the Joint Research Centre of the European Commission organized a workshop with relevant stakeholders, mainly researchers in the field and representatives from city authorities, initiating the process of defining general vehicle classes and the level of detail for the generic numerical models of vehicles. The workshop allowed for the collection of considerations and know-how of various stakeholders and set up a forum for collaboration in the field. The participants agreed that there is a need to employ numerical simulations in the evaluation of the performance of the protective measures in hostile vehicle mitigation. All participants agreed that there is a big need to employ numerical simulations in the evaluation of the performance of the protective measures in hostile vehicle mitigation. Cheap solutions can support local authorities that suffers from significant budget limitations due to the COVID 19 crisis. The availability of generic models might allow much cheaper development costs of barriers. On the technical level the main conclusion was that simplifications of the numerical model can increase the computational efficiency. The simplified models should be validated against more detailed models and physical tests (when possible). Two important aspects that should be considered in the simplification procedure are 1) the simplified model should be able to capture the kinematics of the vehicle (running or rolling over the barrier) and 2) formation of fragments and penetration distance. It has been agreed that a guideline document for numerical simulations in hostile vehicle mitigation can be very useful for the analyst. Also a better representation of the numerical techniques in the existing certification standards would facilitate their use. A short survey collecting opinion on the needs of developing generic models for hostile vehicle mitigation is available here. On the basis of these discussions, JRC will propose to create general numerical models respective to the existing vehicle classes. For more information, please contact JRC-PUBLIC-SPACES@ec.europa.eu References - Karlos V., Larcher M., Solomos G. “Guideline Selecting proper security barrier solutions for public space protection”, JRC Technical Report, JRC113778, 2018
- Action Plan to support the protection of public spaces, COM(2017) 612, European Commission, 2017.
- Valsamos G., Larcher M., Casadei F., Karlos V. “A numerical framework to support the certification of barrier testing”, JRC Technical Report, JRC120307, 2020
- International Organization for Standardization, Vehicle Security Barriers-Part 1: Requirement, Vehicle impact test method and performance rating, IWA 14-1, Vernier, Switzerland, 2013.
|

|
|
|
|
|
|
Good examples
|

|
|
Interview with authorities from the city of Nice, France: implementation of technological solutions for the protection of public spaces
|
|
The city of Nice, France has become a European pioneer in the implementation of technological solutions for the protection of its public spaces. Urban authorities have successfully adopted hi-tech protection without hampering the charm and livability of the Côte d’Azur capital city.
We talk to Sébastien Viano, Director of the European Affairs and External Funding of the Metropole Nice Côte d’Azur and coordinator of the EU Urban Agenda Partnership on Security in Public Spaces.
|
|
|

|
|
The city of Nice, France has become a European pioneer in the implementation of technological solutions for the protection of its public spaces. Urban authorities have successfully adopted hi-tech protection without hampering the charm and livability of the Côte d’Azur capital city. Nice’s Urban Supervisory Control Centre is one of the largest videoprotection complexes in Europe serving multiple purposes: from issuing traffic fines and managing traffic flows to protection from natural disasters, crime and terrorist attacks. Police patrols are geolocated at all times, public buildings are equipped with alarms connected to the Supervisory Control Centre and citizens are engaged through a neighbourhood watch alert system. We talk to Sébastien Viano, Director of the European Affairs and External Funding of the Metropole Nice Côte d’Azur and coordinator of the EU Urban Agenda Partnership on Security in Public Spaces. 
Copyright: Freesurf @ stock.adobe.com Q: What technological solutions do you apply in the city of Nice for ensuring the protection of public spaces? A: The city of Nice has always used state-of-the-art tools for the protection of its population and particularly of its public spaces. This notion of "state-of-the-art" technology must, however, be compatible with the legislation in force, legislation which often lags behind technological progress. In a sustainable way, the city of Nice is now deploying a video protection system equipped with HD, 360°, thermal cameras equipped with software for the detection of, for example, suspicious packages, people groupings or intrusions. The city of Nice is also equipped with LAPI devices to control access to certain reserved areas. More recently, the city of Nice has deployed call points positioned on the public highway allowing all citizens to instantly and geolocally report a problem they witness. More specifically, the city of Nice has deployed an "alert button" system available to all municipal buildings, schools, daycare centers, theaters, as well as all businesses and professionals who have requested it: when triggered by its owner, it allows the user to connect directly to the supervision center, to geolocate the user and to control the city's camera network towards the place where the event is taking place. The city of Nice has also set up a connected network of "vigilant neighbours" channels over the last ten years to provide citizens with information on matters relating to public safety. More specifically, municipal police officers are equipped with a pedestrian camera system whose purpose is to capture the images and sound of an intervention, with various purposes of prevention, training or even criminal prosecution. Finally, the city of Nice has a public transport network that is fully connected to the municipal police command centre in real time, via a video protection system but also via interoperable systems. On a more ad hoc basis, the city of Nice regularly implements experiments. For example, in 2019 it was the first European city to deploy a facial recognition experiment on the public highway, which was very conclusive but could not be renewed or extended due to overly restrictive national legislation. More recently, it has attempted to deploy a citizen security application system aimed at putting the citizen at the heart of security co-production, a system that has not been approved by the CNIL (the national data protection authority). Q: What are the main benefits you have noted from the implementation of technological solutions for the protection of public spaces? A: The use of the above-mentioned equipment has had a huge impact on the security of public spaces, making them ever safer. Street delinquency has decreased by 40% in the last 10 years. The clearance rate has increased by 400%. The actions of pickpockets have dropped by 50% in the public transport networks. The delinquency related to door robberies has been totally eradicated. Technology has come to reinforce human action: these results are supported by the implementation of a global security policy in which technology has become an essential link. Q: How do you decide what technological solutions to adopt? What are the considerations you take into account during the decision-making process? A: The equipment deployed by the city of Nice on a permanent basis has always been the subject of reflection based on expertise in the fields of public safety, IT security, guaranteed data protection and, above all, the existence of a legal framework enabling their implementation and deployment. Experiments aim to assess the impact of technologies on the operational, technical and data protection levels, but are only very rarely allowed in France in view of the legislation in force. Q: Did the implementation of technological solutions require changes in the organization of your work? A: The implementation of technological solutions has obviously changed the organisation of work in many aspects (technical, operational, etc.) The co-production of security (State, city, private actors, citizens) is at the heart of daily security for global security. An evolution of employment frameworks is also to be noted where specific skills are required, particularly for video protection operators (specific training). Q: How do you ensure the coordination, cooperation and communication among the various security actors and stakeholders? A: The system of governance has evolved: at a time when the territories have the technologies, the State relies on them to implement global security policies. The territories have become key players in the co-production of security and the implementation of "BIG DATA" and its sharing makes it possible to contribute more and more each day. Q: Could you describe some concrete problems you have faced in the implementation of technological solutions for the protection of public spaces? A: For a technology to be used effectively for security purposes, it must respond favourably to several aspects: technical - it must work; operational - it must be useful for the purpose; and legal - the data collected must be protected. On the technical level, in the early days of video protection, the quality of image flows or the absence of 360° cameras could represent an obstacle to the proper protection of public spaces: the pitfall of not being able to view certain scenes was in fact recurrent. At the operational level, when implementing a system, the beginnings are sometimes complex because of the novelty of the tool and the adaptation of working methods to it. For example, the deployment of a videoprotection network in public transport had to be understood by the agents of the command centre or in the field and their coordination was the key to the success of the system. From the legal point of view, it is important that the system is able to meet the legal framework in force, particularly in terms of data protection, storage and processing. For example, French law allows videoprotection streams to be kept for a maximum period of one month when, for reasons of storage space in order to guarantee data security, the city of Nice decided to keep them for ten days. Q: Do you think exchange of data among urban authorities in the EU is feasible? Would it be beneficial? What challenges have to be addressed in order to allow for such cooperation? A: The exchange of data between European territories appears not only beneficial but also essential to meet the challenges of everyday security issues. At a time when threats are constantly increasing and when the free movement of people and goods within the European territory is a fundamental freedom for European Union citizens, the security of the territory is at stake. How can it be imagined that border territories where trade is possible at any time cannot have the same knowledge of risks or the same ability to protect themselves against them? There are many challenges, but they can only really be met when the territories are recognised by Europe as key players in security policies and as privileged interlocutors of the European Union. Note from the editor: Low Access Priority Indicator devices provide the registration of data during machine-to-machine communication (for example radio-wave emitter in a vehicle sending signal to a control access system). |

|
|

|

|
|
The European Forum for Urban Security, a network dedicated to the security of public spaces
|
|
Founded in 1987, The European Forum for Urban Security (Efus) brings together nearly 250 cities and regions from 15 countries. It is the only European network dedicated to fostering discussion, cooperation and support among local and regional authorities in the field of crime prevention and urban security.
|
|
|

|
|
Recognised for its expertise by national and European institutions, Efus is a network that represents the diversity of territories and promotes the exchange of experience between local authorities beyond political divisions, according to the principle of “cities helping cities”. Its objectives are as follows : - To promote a balanced vision of urban security combining prevention, sanctions and social cohesion
- To support local and regional authorities in the design, implementation and evaluation of their local security policy
- To reinforce the role of local elected officials within national and European governance
The principle of co-production and the choice of prevention that underlie Efus’ activities are expressed in the “Security, Democracy and Cities” manifesto. This manifesto is the result of a collective writing and is based on the work conducted by Efus, its members and its entire network (universities, European and international organisations, thematic networks). Efus’ members will renew their commitments during the next “Security, democracy and cities” international conference that will take place in Nice in spring 2021, which will lead to an updated manifesto. The central issue of public spaces in urban security policies For over 30 years, Efus has been working on cross-cutting topics linked to urban security such as nightlife, risky behaviours, street violence, violence against women, large events… with the overarching notion of public spaces always at the heart of its reflexion. While citizens occupy these vital areas of urban life for communication, meetings, political demonstrations, artistic and cultural performances and all sorts of entertainment, they are also vulnerable to a multitude of issues: incivilities, conflicts of use between different categories of the population and difficulty to fully secure such places during large gatherings or events, especially against terrorist threats. These characteristics give public spaces a specific status in the domain of urban security: effectively, they require a security policy that is based on genuine cooperation between the different organisations and institutions concerned (local authorities, local police, emergency services, public spaces agents, private security operators, user representatives…), for instance a co-production of security that guarantees that this type of urban place is both safe and open and accessible for everyone. The role of local and regional authorities European cities play a central role in promoting a shared culture of security issues and are confronted with similar challenges regarding their public spaces. They are particularly well-placed to organise the co-production of security with all the relevant stakeholders in order to promote the participation of local communities in the design and management of their public spaces. Furthermore, security practices can be transposed from one city to another across Europe and the sharing of experiences contributes to improving local action but also to creating a collective knowledge. In this objective, Efus, with the cities of Nice (France) and Madrid (Spain), is coordinating the new partnership on the security in public spaces of the Urban Agenda for the EU, that aims at affirming the role of cities in European security policy on public spaces. Through this three-year partnership, European local and regional authorities, Member States and institutions will work together to strengthen the role of cities in European urban security policies, increase the sharing of knowledge and good practices, and advocate at European level legislative reform and new funding frameworks. This partnership is in line with the European Commission Action Plan to support the protection of public spaces, according to which “local and regional authorities are [...] important stakeholders in the protection of public space”, whose involvement must be reinforced by promoting dialogue and exchange between national, regional and local authorities and supporting the development of operational projects.* Developing partnerships to address current issues As they play a leading role in the reflection on smart cities and on the contribution of new technologies to the security of public spaces, local authorities must maintain their dialogue and partnership with research and industries that provide solutions. In order to provide global and tailor-made solutions to public space issues, local security policies must include local, multi-stakeholder diagnosis. In this objective, Efus is a partner in a number of european projects that develop security solutions for public spaces, such as the Cutting Crime Impact project on the development of tools for the prevention on crime for local police forces and authorities, and the Secu4All project, which seeks to train and make local local authorities and relevant actors aware of their role in the design, planning and management of public spaces. Efus is also a partner in the PACTESUR and PRoTECT projects, which aim to strengthen local authorities’ capabilities in public space protection against terrorist threats. Within the framework of its activities, the PRoTECT Consortium organised a three days seminar focusing on technological and human-centred solutions to protect public spaces against terrorist threats on 15, 16 and 17 of July. Efus also coordinates a working group on Security & Innovation, that seeks to harness the opportunities of smart and hyper connected cities to improve crime prevention and urban security. The use of new technologies is particularly important to discuss in order to ensure that local authorities choose the most appropriate technology according to their specific local context and the needs of their population while ensuring that fundamental freedoms are respected. In order to promote the exchange of experiences amongst peers, Efus has launched a new series of web conferences on new technologies in urban security, in order to share prospective reflections and insights on innovative strategies, both in the social and technological realms, that can be applied to urban security. > Learn more about Efus ----------------------------------- * European Commission, Action Plan to Support the Protection of Public Spaces, COM, 2017
|

|
|

|

|
|
Launch of the Horizon 2020 funded project: S4ALLCities - Smart Spaces Safety and Security for All Cities
|
|
The project integrates advanced technological and organisational solutions in a market oriented unified Cyber – Physical Security Management framework aiming at increasing the resilience of cities’ infrastructures, services, ICT systems, IoT and at fostering intelligence and information sharing among city’s security stakeholders
|
|
|

|
|
Smart Cities require “All Time Assurance” for the safety and security of citizens using smart spaces, operational systems and services. These may include smart cities’ main infrastructures such as transport hubs and networks, energy and water supply networks; hospitals as well as spaces with public character such as malls, open markets, pedestrian precincts, city squares, sports venues, concert halls, tourist sites and so forth. With the continuous advancement of Smart City technologies and particularly with the proliferation of IoT Technologies, hundreds of thousands of connected systems are being embedded in many cities’ critical infrastructures enabling city executives, urban planners and security managers to improve their operations and the lives of their citizens in real-time. While these emerging technologies are bringing increased operational efficiencies, smart city infrastructure is also vulnerable to new threats and attacks. S4ALLCities is a project funded by the European Union’s Horizon 2020 call for proposals H2020-SU-INFRA-2019 (Protecting the infrastructure of Europe and the people in the European smart cities), with a duration of two years (September 2020 – August 2022). The S4ALLCities project integrates advanced technological and organisational solutions in a market oriented unified Cyber – Physical Security Management framework, aiming at increasing the resilience of cities’ infrastructures, services, ICT systems, IoT and fostering intelligence and information sharing among city’s security stakeholders. S4ALLCities will deploy and validate intelligent components and functionalities on actual environment, ensuring the delivery of solutions and services in line with smart cities emerging requirements, focused on: risk-based open smart spaces security management; cyber security shielding; suspicious activity and behaviour tracking; identification of unattended objects; real-time estimation of cyber-physical risks in multiple locations and measures activation for effective crisis management. The technologies of S4AllCities will be demonstrated and tested in situ in three major European pilot Smart Cities Spaces with their selected critical infrastructure networks, within crowded places and the participation of local security forces concerned. These include 1- The City of Bilbao, Spain; 2- The Municipality of Trikala, Greece, 3- The City of Pilsen, The Czech Republic, supported also by two additional European Cities, namely 4- The City of Valencia, Spain and; 5- The City of Buzau, Romania. Emulated security breach scenarios based on real-use cases will demonstrate S4AllCities’ technologies effectiveness in confronting threats like: - placement of explosives or other dangerous and harmful substances within transport infrastructures,
- remote access to transport infrastructure (e.g. cyber-attack on the remote piloting system of an autonomous bus),
- suspicious activities of individuals or groups of people in open spaces that may indicate preparatory activities towards the realization of a major crisis (sabotage of infrastructures and facilities),
- automated detection of explosives and suspected armed attackers during mass gathering events such as football matches or festivities,
- dangerous chemical leakage due to accident or terrorist attacks.
The multinational consortium (27 public, private and research entities from 9 European countries) will adapt the project’s innovative technological systems into a market-ready and cost-efficient integrated solution. S4AllCities exploitation phase will promote good practices and guidance material across EU cities so as to enhance capacity building of involved stakeholders, reduce the vulnerabilities of public spaces, mitigate the consequences of adversary attacks, raise public awareness and strike a balance between improving security and preserving the open nature of public spaces as well as citizens’ freedom. The project is coordinated by the Greek-based company EXUS Software and is mainly driven by nine SMEs that bring in significant commercial expertise, supported by large applied research institutes, highly esteemed universities with proven research background on the field and nine public administrations, critical infrastructure operators and law enforcement agencies. For more information and participating organisations: https://cordis.europa.eu/project/id/883522
|

|
|

|

|
|
Launch of a Horizon 2020 Funded Project: IMPETUS Intelligent Management of Processes, Ethics and Technology for Urban Safety
|
|
An innovative project to enhance the resilience of smart cities in the face of security threats in public spaces.
|
|
|

|
|
IMPETUS: Intelligent Management of Processes, Ethics and Technology for Urban Safety is a newly launched project funded by the Horizon 2020 programme of the European Commisison. The goal of IMPETUS is to provide city authorities with new means to address security issues in public spaces. Using data gathered from multiple sources, the project aims to facilitate detection of threats and help human operators dealing with threats to make better informed decisions. The IMPETUS approach addresses three complementary but overlapping areas: - Technology: Leverage the power of Internet of Things (IoT), Artificial Intelligence (AI) and Big Data analysis to provide powerful tools to manage physical and cyber security in cities.
- Ethics: Balance potentially conflicting needs to collect, transform and share large amounts of data with the imperative of ensuring protection of data privacy – all in the context of ensuring benefits to society.
- Processes: Define cognitive processes and deployment guidelines supporting decision making and coordination, fully aligned with the needs of multiple city stakeholders involved in security operations.
IMPETUS will detect potential threats by using AI techniques to search social media and the deep/dark web for unusual and suspicious activities, and to analyse available smart city data. Threats will be classified and assessed to determine an appropriate response using an approach which employes the power of AI to support human judgement. The project will build on tested technologies but enhance and combine them in a coherent and user-centred solution that goes beyond state-of-the-art in key areas such as detection, simulation & analysis and intervention. The IMPETUS consortium consists of 17 partners from 11 different EU Member States and Associated Countries. It brings together 5 research institutions, 7 specialist industrial and SME companies, 3 NGOs and 2 local government authorities. The consortium is complemented by COSSEC (Community of Safe and Secure Cities) – a group that the project will establish and foster. COSSEC will be made up of end-users and other stakeholders able to provide feedback on IMPETUS solutions as they are being developed, and to promote the IMPETUS approach more widely. Major on-street trials will be held in the cities of Oslo, Norway and Padova, Italy. The project receives financial support of 8 M€ from the Horizon 2020 programme for research and innovation of the European Commission. It started in September 2020 and will last for two years. If you want to know more about IMPETUS please contact:
Project Coordinator: Joe Gorman, SINTEF Digital, Joe.Gorman@sintef.no
Dissemination Manager: K. Harald Drager, TIEMS, khdrager@online.no |

|
|
|
|

|

|
|
Report from the International Union of Railways workshop on 'The Impact of Covid-19 on Security'
|
|
The International Union of Railways (UIC) is the worldwide organisation for international cooperation among railways and promotion of rail transport at a global level. Founded in 1922 in Paris, France, it currently gathers about 200 members on all 5 continents.
|
|
|

|
|
The International Union of Railways (UIC) is the worldwide organisation for international cooperation among railways and promotion of rail transport at a global level. Founded in 1922 in Paris, France, it currently gathers about 200 members on all 5 continents, among them railway operators, rail infrastructure managers, railway service providers, public transport companies, etc. UIC maintains close cooperation links with all actors of rail transport, including industries, railway associations and public authorities. Within UIC, the Security Division contributes to anticipate threats and vulnerabilities to the railway system ahead of time (from minor daily crime to major terrorist attacks), to ensure comprehensive protection of railway activities and strengthening the resilience of systems and organisations. On 17 June, the security division of UIC organised an online workshop focussing on the impact of Covid-19 on Security. More than 50 participants from 20 countries in Europe, Asia and America participated. The audience was composed of security experts from railways as well as representatives from authorities, international organisations and European Commission. This workshop complemented the meetings of the UIC Covid-19 taskforce which are taking place every 2 weeks, with special focus on the impacts of Covid-19 measures on security during and after the lockdown period. Marc Guigon, UIC chair of the Covid-19 task force composed of 70 UIC members and 18 International organisations, presented all the outputs of this task force and especially the produced guidances which demonstrate the rail sector RAILsilience (online at https://uic.org/covid-19/). The goal of the workshop was to address security aspects of the Covid-19 crisis. The workshop was a great opportunity to learn more on the cooperation between railways and authorities in India (Railway Protection Force), Canada (Via Rail Canada) and France (French transport ministry). Then the impact on security of the crisis in Germany, Italy and Poland was presented respectively by security managers from DB, FS and PKP. The presentations showed how challenging it is to have such a long crisis and to adjust the organisation accordingly, especially security skills which need to be adapted to the pandemic. Partnerships with authorities is also a key aspect of the crisis, especially with regards to the enforcement of some measures such as wearing masks, social distancing or measuring the temperature of the passengers. In many countries, the total number of security related incidents has decreased since the number of passengers was very low during the confinement period. However, when resuming operations with enforcement of measures such as facial masks, more verbal or physical aggressions towards staff could arise. The main challenge is to restore passenger confidence and to assure their feeling of security as traffic is resuming. In this context, almost all rail organizations adopted a three pillars action plan; continuous prevention, communication and visibility of actions: - Continuous prevention: rail organizations are continuing for the foreseeable future to apply the preventive measures adopted during the peak of the pandemic including disinfection and cleaning, enforcing social distancing measures, promoting hygiene best practices and avoiding overcrowding in trains and stations. Rail organizations are also actively investigating new innovative solutions to help fight the pandemic (new disinfection protocols, new technologies to facilitate the enforcement of social distancing, etc.)
- Communication is obviously a key element in regaining the trust of customers. Organizations are continuing to communicate updates and messages related to the Covid-19 situation at all points of interaction with passengers (starting from sales till the end of journey), as well as, launching specific communicationcampaigns to highlight the efforts made by companies to ensure the safety of rail transport beyond the regular measures put in place, such as investing in research to know more about the spread in transportation or the extra effort put in new technologies and the use of innovative solutions (e.g. enhanced ventilation, ultraviolet light disinfection etc.)
- Visibility of action: one of the most important strategies is to make the organizations’ actions and effort visible to the eyes of customers during their daily travel. Passengers seeing the staff performing the safety measures in real life plays a crucial role in regaining their trust, actions like active cleaning and disinfection, security personnel making sure that passengers are respecting social distancing and prevention measures, uncrowded trains due to a conservative sales strategy, etc.
Given the success of the workshop, which was very interactive with many exchanges between the participants, it was decided to organise another security dedicated workshop after the summer break to have an update on the situation while many railways are resuming almost fully operations. If you would like to have further information, you can contact Marie-Hélène Bonneau (bonneau@uic.org)
|

|
|
|
|
|
|
Publications
|

|
|
Guideline on Building perimeter protection. Design recommendations for enhanced security against terrorist attacks.
|
|
The Joint Research Centre of the European Commission has published a guideline document with practical advice on the selection and installation of elements that are able to stop and/or deter potential terrorist attacks.
|
|
|

|
|
The Joint Research Centre of the European Commission has published a guideline document with recommendations for a robust and usable approach for the physical protection of infrastructures against potential terrorist attacks. It addresses the needs of security and law enforcement officials, building/site owners, venue organizers, state organizations, engineers and other stakeholders that are in charge of securing facilities and critical infrastructures against the terrorist threat. The guideline provides a methodology for securing buildings against intruders, terrorists and other physical threats that try to intrude or gain access to a vulnerable asset. The focus is on the introduction of concepts that are applicable to the design of building security and aim in protecting people and property by enforcing a security perimeter. It illustrates a detailed analytical procedure for identifying the weaknesses of potential terrorist targets and for assessing the relevant risk for different terrorist tactics. It provides advice on the introduction of protection measures against both external and internal explosions and on minimizing the likelihood for the development of a progressive collapse mechanism. It proposes specialized perimeter physical protection measures which can successfully restrict unauthorised vehicle and intruder access, supplemented by the employment of modern digital technologies, such as video surveillance, smart sensors and video analytics. A chapter also sheds light to key issues and possibilities that are provided by the proliferation of new digital technologies. The guideline also addresses the threat posed from the malicious use of Unmanned Aircraft Systems and calls for a holistic building security scheme. The guideline is free available here: https://publications.jrc.ec.europa.eu/repository/handle/JRC121582
|

|
|

|

|
|
Leitfaden Auswahl geeigneter Durchfahrtssperren zum Schutz des öffentlichen Raums
|
|
Schutz vor Anschlägen mit Fahrzeugen
|
|
|

|
|
Dieses Dokument dient als Leitfaden für die Gestaltung, Prüfung und Installation von Fahrzeugsperren zum Schutz öffentlicher Räume vor Terroranschlägen und anderen Arten extremistischer Anschläge mit Fahrzeugen. Es ist festzustellen, dass öffentliche Räume wie Straßenmärkte, Jahrmärkte, Sehenswürdigkeiten, Fußgängerzonen und öffentliche Plätze in den letzten Jahren immer wieder das Ziel von mit Fahrzeugen verübten Anschlägen waren, so z. B. in Nizza, Barcelona, London, Berlin, Stockholm, New York und Toronto. In diesem Dokument werden Defizite in der Konstruktion derartiger Sicherungslösungen aufgezeigt. Ziel ist die Erstellung eines einfachen, unabhängigen Praxisleitfadens, der es Sicherungsbeauftragten ermöglicht, eine vorbereitende Untersuchung von Elementen durchzuführen, die mögliche Terroranschläge stoppen und/oder verhindern können. Zur Beurteilung des jeweiligen Risikos wird ein ausführliches analytisches Verfahren erläutert. Dieses dient der Feststellung der Schwachstellen öffentlicher Räume gegenüber derartigen Anschlägen und der Berechnung der Parameter, die die Geschwindigkeit eines Bedrohungsfahrzeugs beeinflussen, bevor dieses in einen zu schützenden Bereich eindringt. Außerdem werden Empfehlungen für die Auswahl angemessener schützender Sperren gegeben, die durch Unterschiede bezüglich der Leistungsbewertung, Kosten, Wirkungsmechanismen, Attraktivität und dauerhafte oder temporäre Nutzung gekennzeichnet sind. Ein besonderes Augenmerk wird auf das Erscheinungsbild der Sperren und deren harmonische Integration in das urbane Umfeld nach einem konzeptionsintegrierten Sicherungskonzept gelegt, um ein Gleichgewicht zwischen der freien Zugänglichkeit öffentlicher Räume und deren Absicherung zu erreichen. Der Leitfaden ist in Englisch, Französisch und nun auch in Deutsch erhältlich. Interessierte können diese beziehen über JRC-PUBLIC-SPACES@ec.europa.eu. This is the German translation of the Guideline “Selecting proper security barrier solutions for public space protection” and can be requested in English, French and German via JRC-PUBLIC-SPACES@ec.europa.eu.
|

|
|
|
This newsletter is published under the initiative of DG HOME and JRC.
If you would like to share news, events or to contribute with an article, please contact us at HOME-D2-TERRORISM@ec.europa.eu or JRC-PUBLIC-SPACES@ec.europa.eu
If this newsletter was forwarded to you and you are interested to receive it directly you can subscribe here.
You may unsubscribe from this newsletter by going to your profile or by contacting us at this address: JRC-PUBLIC-SPACES@ec.europa.eu
Catalogue Number KJ-BG-19-001-EN-N (online)
|
|

|
|